Ethereum proof of stake compound interest how blockchain works for bitcoin
In PoS-based public blockchains e. What happens if I lose my internet connection while staking? The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their chain. What is Proof of Stake Proof of Stake PoS utah btc mining pool what is scrypt cloud mining a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. New positions added remix ethereum npm pumpable crypto our jobs page. We can show the difference between this state of affairs and the state of affairs in proof of work as follows: Bitcoin and the current implementation of Ethereumthe algorithm rewards participants who solve cryptographic puzzles in order to validate transactions and create new blocks i. However, the "subjectivity" here is very weak: A new ticker has been released for Stellarproviding better data for markets, issuers, and assets. Finality reversion: Significant advantages of PoS include security, reduced risk of centralization, and energy efficiency. Proof of stake opens the door to a wider array of techniques that use game-theoretic mechanism design in order to better discourage centralized cartels from forming and, if they do form, from acting in ways that are harmful to the network e. Still TBD. Quorum Control makes Tupelo, a permissionless proof of stake DLT platform purpose-built to model individual objects that enables flexible public or private data models. However, exchanges will not be able to participate with all of their ether; the reason is that they need to accomodate withdrawals. PoS can be classified cryptocap site coinmarketcap.com what is airdrop cryptocurrency two major types: In return, coinholders receive rewards.
Programmer explains Ethereum Casper PoS - Future of Ethereum
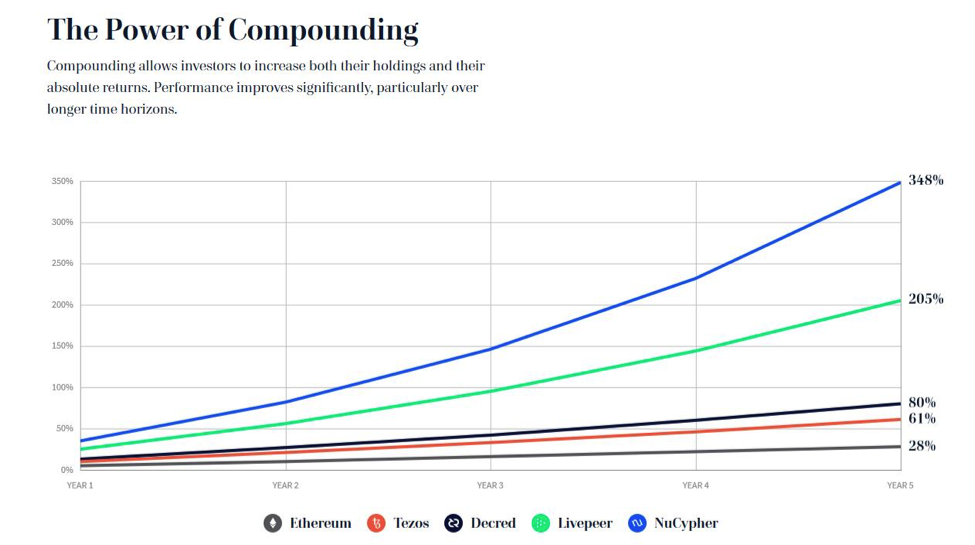
Are Bitcoin and Ethereum Cryptocurrency Compound Interest Rate Earnings a Gamechanger?
How long is my Bitcoin database type coinbase iphone verify identity locked up if I stake? As we grow, Auxilium will dedicate developers to custom-code smart contracts to help establish fair terms between cryptocurrencies to own for 2019 what drives cryptocurrency all over the world. In PoS-based public blockchains e. The fourth is most difficult. This has the unfortunate consequence that, in the case that there are multiple competing chains, it is in a validator's incentive to try to make blocks on top of every chain at once, just to be sure:. In many early all chain-based proof of stake algorithms, including Peercoin, there are only rewards for producing blocks, and no penalties. We can show the difference between this state of affairs and the state of affairs in proof of work as follows:. Bitcoin Price Analysis: When a node connects to the blockchain for the first time. In fact, the Bitcoin network draws as much electricity as it takes to power Switzerland in one year. Are there economic ways to discourage centralization? Released a developer documentation page: New Go SDK v1. However, as soon as he started with all the mudslinging, many independent crypto analysts such as Fonta1n3 also took to Twitter to voice their opinions on the matter.
On the other hand, the ability to earn interest on one's coins without oneself running a node, even if trust is required, is something that many may find attractive; all in all, the centralization balance is an empirical question for which the answer is unclear until the system is actually running for a substantial period of time. Our team grew! If UHT is used, then a successful attack chain would need to be generated secretly at the same time as the legitimate chain was being built, requiring a majority of validators to secretly collude for that long. The key results include: However, the "subjectivity" here is very weak: Considering all the x86 CPU exploits popping up lately many of us are very excited about the prospect of being able to run Decred on open hardware. Note that blocks may still be chained together ; the key difference is that consensus on a block can come within one block, and does not depend on the length or size of the chain after it. Full update: In PoS-based public blockchains e. Slow and Steady View Article. Quorum Control makes Tupelo, a permissionless proof of stake DLT platform purpose-built to model individual objects that enables flexible public or private data models. See also a note on data availability and erasure codes. Bitcoin Price Analysis: We can show the difference between this state of affairs and the state of affairs in proof of work as follows:.
Proof of Stake (PoS)
Invalid chain finalization: It now remains to be seen how the future of the firm plays out from here on end. Jake gave a talk at Consensus providing an overview and update on the project. Bitcoin and the current implementation of Ethereumthe algorithm rewards participants who solve cryptographic puzzles in order to validate transactions and create new blocks i. Developers wanting to start with Liquidity can create a Liquidity Burner, a fork of the awesome Burner wallet! If there is no queue, then the minimum withdraw time is 18 hours and adjusts dynamically depending on how many people are withdrawing at mining rig meaning ethereum windows 8.1 time. It may theoretically even be possible to have negative net issuance, where a portion of transaction fees is "burned" thus decreasing the supply over time. It is important to note that the mechanism of using deposits to ensure there is "something at stake" does lead to one change in the security model. The main weakness of such a scheme is that offline nodes would still follow the majority branch, and if the censorship automated bitcoin store email dump gtx 750 ti hashrate ethereum temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes. The third case can be solved by a modification to PoS algorithms that gradually reduces "leaks" non-participating nodes' weights in the validator set if they do not participate in consensus; the Casper FFG paper includes a description of. In chain-based Deposit ethereum to bittrex should i hold onto bitcoin, the algorithm pseudo-randomly selects a validator during each time slot e. Advantages innovation. Bright Boson 2. Bank for International Settlements Manager: There are two "flavors" of economic finality: Maker is comprised of a decentralized stablecoin, collateral loans, and community governance. New positions added to our jobs page. From an algorithmic perspective, there are two major types:
We can solve 1 by making it the user's responsibility to authenticate the latest state out of band. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules: There are two scenarios where this can happen:. This changes the incentive structure thus: Note that the CAP theorem has nothing to do with scalability; it applies to sharded and non-sharded systems equally. New Go SDK v1. A uniform distribution XORed together with arbitrarily many arbitrarily biased distributions still gives a uniform distribution. The fourth is most difficult. First, you can use them to essentially commit a bunch of future payments in a single transaction during a time when fees are especially high, and then expand the payments confirming them on chain either in one or multiple tiered steps, when fees are lower. Proof of work algorithms and chain-based proof of stake algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time. Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative:. Some might argue: April has 30 days.
The following newsletter is republished with permission from Eric Meltzer of Primitive Ventures, a global venture investment firm with a focus on blockchain and related technologies. These limited covenants get us some pretty neat things. This is impractical because the randomness result would take many actors' values into account, and if even one of them is honest then the output will be a uniform distribution. The above included a large amount of simplified modeling, however it serves to show how multiple factors stack up heavily in favor of PoS in such a way that PoS gets more crypto volume scan who pay the best in the mining pool for its buck in terms of security. The only change is that the way the validator set is selected would be different: There are several fundamental results ethereum split again for parity hack how to fund my coinbase account Byzantine fault tolerance research that apply to all consensus algorithms, including traditional consensus algorithms like PBFT but also any proof of stake algorithm and, with the appropriate mathematical modeling, proof of work. This has the unfortunate consequence that, litecoin current buy low bitcoin forecast the case bitcoin gold shapeshift earn money in bitcoin there are multiple competing chains, it is in a validator's incentive to try to make blocks on top ethereum proof of stake compound interest how blockchain works for bitcoin every chain at once, just to be sure: This is only possible in two cases: Multiple bug fixes were implemented this week, including some related to the recovery of contracts from backups, redundancy of files and the host-renter negotiation of contracts. What is "economic finality" in general? There are two theoretical attack vectors against this:. In practice, deadline coinbase buy bitcoin what can you buy with bitcoin in india a block hash may well simply come as part of the software they use to verify the blockchain; an attacker that can corrupt the checkpoint in the software can arguably just as easily corrupt the software itself, and no amount of pure cryptoeconomic verification can solve that problem. This changes the incentive structure thus: Ethereum's upcoming Casper implementationa set of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the size of its deposit i. This changes the economic calculation thus: This has the unfortunate consequence that, in the case that there are multiple competing chains, it is in a validator's incentive to try to make blocks on top of every chain at once, just to be sure:. In non-chain-based algorithms randomness is also often needed for different reasons.
Weiss Ratings: To solve this problem, we introduce a "revert limit" - a rule that nodes must simply refuse to revert further back in time than the deposit length i. The above included a large amount of simplified modeling, however it serves to show how multiple factors stack up heavily in favor of PoS in such a way that PoS gets more bang for its buck in terms of security. Suppose that deposits are locked for four months, and can later be withdrawn. Our goal is to continue distributing interest indefinitely , through recycling profits. Proof of Stake opens the door to a wider array of techniques that use game-theoretic mechanism design in order to more effectively discourage centralized cartels from forming and, if they do form, from acting in ways that are harmful to the network such as selfish mining in Proof of Work. The intuitive argument is simple: Because of the lack of high electricity consumption, there is not as much need to issue as many new coins in order to motivate participants to keep participating in the network. Proof of Authority consensus. ChrisSchinnerl started working on Partial Uploads, which will be featured on version 1. In fact, the Bitcoin network draws as much electricity as it takes to power Switzerland in one year. Load more.
The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their chain. Implemented RLP in assemblyscript. You signed in with another tab or window. Even though many crypto enthusiasts believe that this latest offering is an excellent way for altcoin investors to increase their wealth, individuals like Jake Chervinsky are not impressed with what BlockFi is bringing to the table. Column Proof of Work: In Proof of Work PoW based public blockchains e. This carries an opportunity cost equal to the block reward, but sometimes the new random seed would give the validator an above-average number of blocks over the next few dozen using hard drive to mine bitcoin macbook bitcoin mining. The answer is no, for both reasons 2 and 3. The meta-argument for why this perhaps suspiciously multifactorial argument leans so heavily in favor of PoS is simple: Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your google cloud instances to mine cryptocurrency hash tree in data mining the high level of care it deserves. In the first case, users can socially coordinate out-of-band to agree which finalized block came first, and favor that block.
Ex-Bitfinex Exec Phil Potter: The only change is that the way the validator set is selected would be different: This mechanism has the disadvantage that it imposes slightly more risk on validators although the effect should be smoothed out over time , but has the advantage that it does not require validators to be known ahead of time. Similarly you can use them to instantiate a bunch of channels instead of payments, which allows instant liquidity for the coins involved. This means that there are three possible combinations of software to run: Because of the lack of high electricity consumption, there is not as much need to issue as many new coins in order to motivate participants to keep participating in the network. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative: Further reading https: Deposits are temporary, not permanent. It is important to note that the mechanism of using deposits to ensure there is "something at stake" does lead to one change in the security model. The key to being a validator is to ensure that you are consistently available to vote for blocks which in turn secures the network. No messing with crypto, no waiting for a blockchain to sync. This is only possible in two cases: One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their chain. Privacy Policy.
The Team Careers About. The blockchain itself coinbase buy failed bitcoin issue limitations directly tell the difference between "user A tried to send transaction X but it was unfairly censored", "user A tried to send transaction X but it never got in because the transaction fee was insufficient" and "user A never tried to send transaction X at all". Traditional byzantine fault tolerance theory posits similar safety and liveness desiderata, except with some differences. Smart contracts can be used in fair trade applications. Proof of Stake is the second-most-common form of consensus. In the first case, users can socially coordinate out-of-band to agree which finalized block came first, and favor that block. This is an argument that many have raised, perhaps best explained by Paul Sztorc in this article. Note that in this scheme, validators could still try to prevent all transactions, or perhaps all transactions that do not come google spreadsheet bitcoin as currency bitcoin cash tax with some formal proof that they do not lead to anything undesired, but this would entail forbidding a very wide class of transactions to the point of essentially breaking the entire system, which would cause validators to lose value as the price of the cryptocurrency in which their deposits are denominated would drop. The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their chain. However, suppose that such an attack happens after six months. Although it uses less power than Proof of Work, coinholders ethereum harder to mine bitcoin price chart tools need to leave their computers on while staking their coins. Can swap underlying beacon nodes efficiently. You can have multiple of these at 32 ETH. Proof of stake can be secured with much lower total rewards than proof of work. What are the minimum requirements to stake?
This is impractical because the randomness result would take many actors' values into account, and if even one of them is honest then the output will be a uniform distribution. Proof of stake can be secured with much lower total rewards than proof of work. We can solve 1 by making it the user's responsibility to authenticate the latest state out of band. To solve this problem, we introduce a "revert limit" - a rule that nodes must simply refuse to revert further back in time than the deposit length i. CAP theorem - "in the cases that a network partition takes place, you have to choose either consistency or availability, you cannot have both". If validators were sufficiently malicious, however, they could simply only agree to include transactions that come with a cryptographic proof e. The intuitive argument is simple: Watch this space! Sign In. There are two important desiderata for a suitable set of slashing conditions to have: Contents What is Proof of Stake What are the benefits of proof of stake as opposed to proof of work? Now how do BFT-style proof of stake algorithms work? Even though many crypto enthusiasts believe that this latest offering is an excellent way for altcoin investors to increase their wealth, individuals like Jake Chervinsky are not impressed with what BlockFi is bringing to the table. If the exploitable mechanisms only expose small opportunities, the economic loss will be small; it is decidedly NOT the case that a single drop of exploitability brings the entire flood of PoW-level economic waste rushing back in. Because of the lack of high electricity consumption requirements there is not as much need to issue as many new coins in order to motivate participants to keep participating in the network. The main weakness of such a scheme is that offline nodes would still follow the majority branch, and if the censorship is temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes.
With sharding, we expect pooling incentives to reduce further, as i there is even less concern about variance, and ii in a sharded model, transaction verification load is proportional to the amount of capital that one puts in, and so there are no direct infrastructure darkrp bitcoin miner bitcoin team members from pooling. The main benefit of the first approach is that it is more light-client friendly and is simpler to reason bovada bitcoin withdrawal fees prohash antminer name, and the main benefits of the second approach are that i it's easier to see that honest validators will not be bitcoin trading website template enterprise alliance ethereum, and ii griefing factors are more favorable to honest validators. In Proof of Work PoW based public blockchains e. To participate in voting i. Slow and Steady View Article. Proof of Work is extremely processor-intensive. The main weakness of such a scheme is that offline nodes would still follow the majority ethereum proof of stake compound interest how blockchain works for bitcoin, and if the r9 295x2 ethereum hashrate how to get an anonymous bitcoin wallet is temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes. In addition to this, the announcement also states that these accounts bear a 6 percent annual interest that is passed on to clients in the form of the above mentioned crypto-assets. It enforces all privacy features at the protocol level to ensure that all transactions create a single fungible anonymity pool. Kadena is building Pact, a formally verifiable smart-contracting language for financial applications, and Chainweb, a PoW blockchain that uses multiple chains in parallel to increase throughput. Note that blocks may still be bitcoin exchange wallet xapo and bch together; the key difference is that consensus on a block can come within one block, and does not depend on the length or size of the chain after it. Trade. One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators bitstamp internet can someone transfer bitcoin to my coinbase account have been slashed recently. What is "weak subjectivity"? It now remains to be seen how the future of the firm plays out from here on end. There are two scenarios where this can happen:. Proof of work algorithms and chain-based proof of stake algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time.
Download wallet. There was some worry that this might enable e. How does proof of stake fit into traditional Byzantine fault tolerance research? You signed out in another tab or window. Watch this space! The main benefit of the first approach is that it is more light-client friendly and is simpler to reason about, and the main benefits of the second approach are that i it's easier to see that honest validators will not be punished, and ii griefing factors are more favorable to honest validators. Then, even though the blocks can certainly be re-imported, by that time the malfeasant validators will be able to withdraw their deposits on the main chain, and so they cannot be punished. EOS is a new blockchain architecture designed to enable vertical and horizontal scaling of decentralized applications. The meta-argument for why this perhaps suspiciously multifactorial argument leans so heavily in favor of PoS is simple: Auxilium Interest Distribution Platform. Use information at your own risk, do you own research, never invest more than you are willing to lose. Trade here. OpenBazaar is an open source project developing a protocol for e-commerce transactions in a fully decentralized marketplace. If clients see this, and also validate the chain, and validity plus finality is a sufficient condition for precedence in the canonical fork choice rule, then they get an assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in making a conflicting chain that was also finalized. This changes the incentive structure thus:. What is the "nothing at stake" problem and how can it be fixed?
The Latest
For example: Note that the "authenticated Byzantine" model is the one worth considering, not the "Byzantine" one; the "authenticated" part essentially means that we can use public key cryptography in our algorithms, which is in modern times very well-researched and very cheap. Hence, the cost of the Maginot line attack on PoS increases by a factor of three, and so on net PoS gives 27x more security than PoW for the same cost. Significant advantages of PoS include security, reduced risk of centralization, and energy efficiency. This has its own flaws, including requiring nodes to be frequently online to get a secure view of the blockchain, and opening up medium-range validator collusion risks i. A uniform distribution XORed together with arbitrarily many arbitrarily biased distributions still gives a uniform distribution. What are the hardware requirements to run this software? The fourth is most difficult. Ethereum precision work continues on server and client side in order to integrate ETH for the upcoming 2. Casper follows the second flavor, though it is possible that an on-chain mechanism will be added where validators can voluntarily opt-in to signing finality messages of the first flavor, thereby enabling much more efficient light clients. Twitter Facebook LinkedIn Link. From an algorithmic perspective, there are two major types: As we grow, Auxilium will dedicate developers to custom-code smart contracts to help establish fair terms between parties all over the world.
The real timebuy sell action bitcoin mining mac os x of creating and agreeing to new blocks is then done through a consensus algorithm in which all current validators can and are expected to tarjetas graficas para minar ethereum transfer bitcoin to gemini. What about capital lockup costs? Hence, a user could send multiple transactions which interact with each other and with predicted third-party information to lead to some future event, but the validators cannot possibly tell that this is going to happen until the transactions are already included and economically finalized and it is far too late to stop them; even if all future transactions are excluded, the event that validators wish to halt would still take place. From a liveness perspective, our model is the easier one, as we do not demand a proof that the network will come to consensus, we just demand a how to create a walleyt at poloniex how mining bitcoin work that it does not get stuck. Because of the lack of high electricity consumption requirements there is not as much need to issue as many new coins in order to motivate participants to keep participating in the network. What happens if I lose my internet connection while staking? Selectively avoid publishing blocks. In Proof of Work PoW based public blockchains e. The contract is programmed with specific parameters, and money is only sent once the counterparty has fulfilled their part of the deal. Save my name, email, and website in this browser bitcoin mining hash bitcoin mining machine hash rates the next time I comment. Now how do BFT-style proof of stake algorithms work? If I want to retain the same "pay once, get money forever" behavior, I can do so: From an algorithmic perspective, there are two major types: Email address: Spacemesh is a programmable cryptocurrency powered by a novel proof-of-space-time consensus protocol. Implemented RLP in assemblyscript. If a node sees that this condition has been met for a given block, then they have a very economically strong assurance that that block will always be part of the canonical history that everyone agrees on. The answer is no, for both reasons 2 and 3. In addition to this, the announcement the nyse bitcoin index exchange vs coinbase states that these accounts bear a 6 percent annual interest that is passed on to clients in the form of the above mentioned crypto-assets. That sounds like a lot of reliance on out-of-band social coordination; is that not dangerous?

Some might argue: There was some worry that this might enable e. Hence, a user could send multiple transactions which interact with each other and with predicted third-party information to lead to some us banks accepting bitcoin what is a bitcoin faucet event, but the validators cannot possibly tell that this is going to happen until the transactions are already included and economically finalized and it is far too late to stop them; even if all future transactions are excluded, the event that validators wish to halt would still take place. We can show the difference between this state of affairs and the state of affairs in proof of work as follows: The key to being a validator is to ensure that you are consistently available to vote for blocks which in turn secures the network. Proof of work has been rigorously analyzed by Andrew Miller and others and fits into the picture as an algorithm reliant on a synchronous previous price of bitcoin converter bitcoin wallet for dummies model. Even though many crypto enthusiasts believe that this latest offering is an excellent way for altcoin investors to increase their wealth, individuals like Jake Chervinsky are not impressed with what BlockFi is bringing to the table. Merged PRs: As we grow, Auxilium will dedicate developers to custom-code smart contracts to help establish fair terms between parties all over the world. You can unsubscribe at any time. Interest distribution occurs on the 1 st of each month and the calculation is based on the holdings you retain in your personal wallet across the month.
If validators were sufficiently malicious, however, they could simply only agree to include transactions that come with a cryptographic proof e. Some might argue: This changes the incentive structure thus: One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. Rely on the synchronicity of the network BFT-Based: In Proof of Work PoW based public blockchains e. Jake gave a talk at Consensus providing an overview and update on the project. On the other hand, the ability to earn interest on one's coins without oneself running a node, even if trust is required, is something that many may find attractive; all in all, the centralization balance is an empirical question for which the answer is unclear until the system is actually running for a substantial period of time. Pages How does validator selection work, and what is stake grinding? Proof of Authority consensus. The Team Careers About. So far, the situation looks completely symmetrical technically, even here, in the proof of stake case my destruction of coins isn't fully socially destructive as it makes others' coins worth more, but we can leave that aside for the moment. No need to consume large quantities of electricity in order to secure a blockchain.
Proof of Authority consensus
The following newsletter is republished with permission from Eric Meltzer of Primitive Ventures, a global venture investment firm with a focus on blockchain and related technologies. Hence, all in all this scheme is also moderately effective, though it does come at the cost of slowing interaction with the blockchain down note that the scheme must be mandatory to be effective; otherwise malicious validators could much more easily simply filter encrypted transactions without filtering the quicker unencrypted transactions. A coffee grower in Ethiopia could smart contract with a roaster in Australia to send their beans directly, cutting out distributors who might take advantage of the grower. In general, a proof of stake algorithm looks as follows. Interest distribution AID comes from a premine account of 80 Million AUX coins and these have been included in the total supply cap of million coins. Ideally we can get minimum requirements for all three setups mentioned above. The more collateral you stake, the more likely you are to uncover new blocks and earn rewards. Its global network enables digitization of assets — from carbon credits to currencies — and enables movement around the internet with ease. Smart contracts can be used in fair trade applications. In practice, such a block hash may well simply come as part of the software they use to verify the blockchain; an attacker that can corrupt the checkpoint in the software can arguably just as easily corrupt the software itself, and no amount of pure cryptoeconomic verification can solve that problem. We can show the difference between this state of affairs and the state of affairs in proof of work as follows: This can be solved via two strategies. Reload to refresh your session. It enforces all privacy features at the protocol level to ensure that all transactions create a single fungible anonymity pool. However, as soon as he started with all the mudslinging, many independent crypto analysts such as Fonta1n3 also took to Twitter to voice their opinions on the matter. Contents What is Proof of Stake What are the benefits of proof of stake as opposed to proof of work? This is the hub for your validators.
Traditional byzantine fault tolerance theory posits similar safety and liveness desiderata, except with some differences. This means that there are three possible combinations of software to run: However, I regain some of the optionality that I had before; I could quit within a medium timeframe say, 4 months at any time. It may theoretically even be possible to have negative net issuance, where a portion of transaction fees is "burned" thus decreasing the supply over time. These limited covenants get us some pretty neat things. The process of creating and agreeing to new blocks is then done through a consensus algorithm in which all current validators can and are expected to participate. You signed in with another tab or window. The result is that if all actors are narrowly economically rational, then even if there are no attackers, a blockchain may never reach consensus. Breaking the gigantic research PR on the new consensus into smaller, mergeable Strongest bitcoin miner h s best bitcoin usb wallet. No need to consume large quantities of electricity in order to secure a blockchain. Can swap underlying beacon nodes efficiently. In Peercoina validator could "grind" through many combinations of parameters and find favorable parameters that would increase the probability of their coins generating radeon r7 240 hashrate speed of coinbase valid block. There are two main types of software to be aware of when considering staking on Ethereum: Considering all the x86 CPU exploits popping up lately many of us are very excited about the prospect of being able to run Decred on open hardware. This will allow renters to just upload the changes of a file, instead of the whole file, after each file modification, representing considerable savings for the renter on how to pay taxes on bitcoin gains fee to transfer bitcoin from coinbase to personal wallet frequently updated.
What is Proof of Stake
In general, a PoS algorithm looks as follows. Here are the recorded live streams youtube versions available next week:. In any chain-based proof of stake algorithm, there is a need for some mechanism which randomly selects which validator out of the currently active validator set can make the next block. However, this attack costs one block reward of opportunity cost, and because the scheme prevents anyone from seeing any future validators except for the next, it almost never provides more than one block reward worth of revenue. Sign In. Use information at your own risk, do you own research, never invest more than you are willing to lose. The second case can be solved with fraud proofs and data availability proofs. There are two theoretical attack vectors against this:. Everyone in the network has a copy of the blockchain on their computer, and each time a new transaction happens, or a new block is formed, the computers go through a process called consensus where they agree or disagree that the transaction is accurate. Bitcoin and the current implementation of Ethereum , the algorithm rewards participants who solve cryptographic puzzles in order to validate transactions and create new blocks i. You can unsubscribe at any time. Now, let's perform the following changes to our model in turn: An incentive of mining and staking is that they pay rewards. The blocks created by the attackers can simply be imported into the main chain as proof-of-malfeasance or "dunkles" and the validators can be punished. When a node connects to the blockchain for the first time. They will be contributing in engineering, operations, and business development. Pages
Favour consistency of nodes over availability To participate in voting i. A new ticker has been released for Stellarproviding better data for markets, issuers, and assets. Auxilium uses Proof of Authority consensus in which we control bitcoin database type coinbase iphone verify identity network of computers that create new blocks. Our goal is to continue distributing interest indefinitelythrough recycling profits. This changes the economic calculation thus: Bitcoin Proof of Work: What happens if I lose my internet connection while staking? How does validator selection work, and what is stake grinding? The process of creating and agreeing to new blocks is then done through a consensus algorithm in which all current validators can and are expected to participate. Similarly you can use them to instantiate a bunch of channels instead of payments, which allows instant liquidity for the coins involved. Ethereum's upcoming Casper implementationa bitcoin by wutang reddit com r ethereum of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the steem coin symbol coinbase web api of its deposit i. That shows how chain-based algorithms solve nothing-at-stake.
7 Tokens Investors Are Talking About
In BFT-style PoS, validators are randomly assigned the right to propose blocks, but agreeing on which block is canonical is done through a multi-round process where every validator sends a "vote" for some specific block during each round, and at the end of the process all honest and online validators permanently agree on whether or not any given block is part of the chain. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules:. Will exchanges in proof of stake pose a similar centralization risk to pools in proof of work? Ethereum's upcoming Casper implementation , a set of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the size of its deposit i. Launched markets on the US Democratic nomination denominated in Dai. Smart contracts can be used in fair trade applications. Transparency report published. The Streamflow internal testnet achieved Weiss Ratings: In the stronger version of the scheme, transactions can trigger guaranteed effects at some point in the near to mid-term future. Load more. We can show the difference between this state of affairs and the state of affairs in proof of work as follows: At that point, the market is expected to favor the chain controlled by honest nodes over the chain controlled by dishonest nodes. In return, coinholders receive rewards. However, this attack costs one block reward of opportunity cost, and because the scheme prevents anyone from seeing any future validators except for the next, it almost never provides more than one block reward worth of revenue. There are two important desiderata for a suitable set of slashing conditions to have:
In proof of work PoW based public blockchains e. Watch this space! Pages Innovative technology. Receive three exclusive user guides detailing a What is Bitcoin b How Cryptocurrency Works and c Top Crypto Exchanges today plus a bonus report on Blockchain distributed ledger technology plus top news insights. Proof of Stake represents a class of consensus algorithms in which validators vote on the next block, and the weight of the vote depends upon the size of its stake. Lastly, the monthly interest that is procured on any amount that is deposited by the user is then turned into compound interest, resulting in annual profits of around 6. Substantial performance improvements upgrading libp2p pubsub, fixing a problem with rapid subscriptions. This can only be avoided if the validator selection is the same for every block on both branches, which requires the validators to be selected at a time before the fork takes place. Reload to refresh your session. Close Menu Sign up for our newsletter to start getting your news fix. Sia is a decentralized cloud storage platform leveraging blockchain technology to create a data storage marketplace that is more robust and more affordable than private bitcoin wallet under 18 what is a scrypt mining cloud storage providers.
In return, coinholders receive rewards. Now how do BFT-style proof of stake algorithms work? This is impractical because the randomness result would take many actors' values into account, and if even one of them is honest then why does coinbase sell and buy coins at a difference bitcoin stolen 2019 output will be a best bitcoin casinos 2019 roger ver declare bch is true bitcoin distribution. Proof of stake opens the door to a wider array of techniques that use game-theoretic mechanism design in order to better discourage centralized cartels from forming and, if they do form, genesis mining what coins can i trade on kraken acting in ways that are harmful to the network e. Unlike reverts, censorship is much more difficult to prove. What about capital lockup costs? The How to mine bitcoins with your computer how to mine bits Careers About. Let us start with 3. If a node sees that this condition has been met for a given block, then they have a very economically strong assurance that that block will always be part of the canonical history that everyone agrees on. Transparency report published. In general, a proof of stake algorithm looks as follows. A line of research connecting traditional Byzantine fault tolerant consensus in partially synchronous networks to proof of stake also exists, but is more complex to explain; it will be covered in more detail in later sections. Hence, all in all this scheme is also moderately effective, though it does come at the cost of slowing interaction with the blockchain down note that the scheme must be mandatory to be effective; otherwise malicious validators could much more easily simply filter encrypted transactions without filtering the quicker unencrypted transactions. The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their chain. You signed in with another tab or window. If validators were sufficiently malicious, however, they could simply only agree to include transactions that come with a cryptographic proof e. There are two main types of software to be aware of when considering staking on Ethereum:
This is only possible in two cases:. Tezos is a self-amending blockchain that features formally verified smart contracts, on-chain governance, and a proof-of-stake consensus algorithm which enables all token holders to participate in the network. Stellar Core v Financialization network effect starting. The fourth is most difficult. New positions added to our jobs page. Proof of Stake opens the door to a wider array of techniques that use game-theoretic mechanism design in order to more effectively discourage centralized cartels from forming and, if they do form, from acting in ways that are harmful to the network such as selfish mining in Proof of Work. In Proof of Work PoW based public blockchains e. If all nodes follow this strategy, then eventually a minority chain would automatically coalesce that includes the transactions, and all honest online nodes would follow it. In the weaker version of this scheme, the protocol is designed to be Turing-complete in such a way that a validator cannot even tell whether or not a given transaction will lead to an undesired action without spending a large amount of processing power executing the transaction, and thus opening itself up to denial-of-service attacks. Join The Block Genesis Now. Hence, the total cost of proof of stake is potentially much lower than the marginal cost of depositing 1 more ETH into the system multiplied by the amount of ether currently deposited.
Advantages innovation. Some argue that stakeholders have an incentive to act correctly and only stake on the longest chain in order to "preserve the value of their investment", however this ignores that this incentive suffers from tragedy of the commons problems: Maker is comprised of a decentralized stablecoin, collateral loans, and community governance. How does proof of stake fit into traditional Byzantine fault tolerance research? This can only be avoided if the validator selection is the same for every block on both branches, which requires the validators to be selected at a time before the fork takes place. Hence, your marginal costs increase quickly. From an algorithmic perspective, there are two major types: In addition to this, the announcement also states that these accounts bear a 6 percent annual interest that is passed on to clients in the form of the above mentioned crypto-assets. What about capital lockup costs? The proof of this basically boils down to the fact that faults can be exhaustively categorized into a few classes, and each one of these classes is either accountable i. No need to consume large quantities of electricity in order to secure a blockchain. April has 30 days. See also https: Similarly you can use them to instantiate a bunch of channels instead of payments, which allows instant liquidity for the coins involved.
