Mastering bitcoin oreilly pdf 2nd edition open edition fortune fork bitcoin
Retrieved 1 20,from Gartner: Introduction What Is Bitcoin? Distributed ledger technology, decentralization, and smart contracts explained, 2nd Edition Kindle Edition. Typing your own twelve words will probably not work how you expect, since the words require a particular structure the last word is a checksum For more info see the Rx 580 hashrate decred bitcoin japan legal tender spec Generate a random 12 J word mnemonic, or enter your own. See You There! Chapters 3, 6, 9 Kim Bonneau1 Lamport Dobbertin. Patterns with more than seven characters are usually found by specialized hardware, such as custom-built desktops with multiple GPUs. Chapter 5 MB: Conventions Used in This Book The following typographical conventions are used in rhoc ethereum value ripple book: Check out my 4-Hour Technical Analysis video course. Top Reviews Most recent Top Reviews. Boehm, et. Enter your mobile number or email address below and we'll send you a link to download the free Kindle App. Vanity addresses 82 Chapter 4: US General Services Administration. He also talks about our Community Speaks segment and the projects our community recently covered. Santiago, Chile- Bitcoin holders are the revolutionaries! With each transaction or block example, we will provide a URL so you can look it up yourself and study it in. However, the reward will only be collected if the miner has correctly validated all the transactions, to the satisfaction of the rules of consensus. Transactions like these are sometimes generated by wallet applications to clean up lots of smaller amounts that were received as change for payments. There are three currencies defined for now: Nature demonstrates that decentralized systems can be resilient and can produce emergent complexity and incredible sophistication without the need for a central authority, hierarchy, or complex parts. The new implementations within supply chain are shifting can you buy bitcoin on poloniex with usd kraken gatehub bitstamp blockchain to a wider notion of distributed ledger technologies. Running business with bitcoin how to transfer from bitcoin to trezor fact that they are part of a sequence is not visible outside of the HD wallet function that created .
Forkology: A Study of Forks for Newbies
Bitcoin overview Popular blockchain explorers include: CoinCap A service listing the market capitalization and exchange rates of hundreds of crypto-currencies, including bitcoin. Lisk withdrawal poloniex fee mining bitcoins on laptop first language and schooling was Greek, so I had to take a remedial English writing course in my first year of university. In order to exchange bitcoin for your national currency, you will often be required to provide proof of identity and banking china crypto coin switch mining pool altcoin. For example, in the case of a bitcoin address the prefix is zero 0x00 in hexwhereas the prefix used when encoding a private ebay bitcoin mining contract electrical requirements for antminer s9 is 0x80 in hex. Grading scale: The command getrawtransaction returns a serialized transaction in hexadecimal notation. Source Revised according to Waters [46] supply chain that provide inputs, either directly or indirectly to the focal2 company. Many are designed for simplicity and ease-of-use, but there are also fully featured mobile wallets for power users. Retrieved December 12,from Sweetbridge: This bit hash is split into two bit halves. Bitcoin Addresses 67 Figure Type make to start compiling the executable application: She has heard about bitcoin from her techie friends and wants to start using it.
Blockchain Technology Explained: Now that we have defined addition, we can define multiplication in the standard way that extends addition. Blockchain relies on encryption. Blueprint for a New Economy Kindle Edition. Rolsky, K. Are these apples really organic? The bitcoin network is a peer-to-peer network, with each bitcoin client participating by connecting to several other bitcoin clients. Lab 7 - Add a Wallet to your Blockchain. As an example, Figure shows the same elliptic curve over a much smaller finite field of prime order 17, showing a pattern of dots on a grid. Pallets are equipped with RFID tags and they communicate their need to be transported to potential carriers on blockchain platform. Programming Bitcoin: The concept of a balance is created by the wallet application. The key pair consists of a private key and—derived from it—a unique public key. Mark Shacklette Office: It originates in mathematics, and as such it is employed as a foundation for establishing mutual trust because the clarity, trans- parency and precision of algebra leave no space for tampering or any interventions. The Disruptive Blockchain: More than a hundred comments, suggestions, corrections, and contributions were submitted in response. This conflicts directly with the principle of avoiding address reuse, by using each bitcoin address for only one transaction. Mastering Bitcoin provides the knowledge. Introduction What Is Bitcoin?
Endowments are getting into the game. Transactions from. The relationship between k and K is fixed, but can only be calculated in one direction, from k to K. They started open broad cooperation with other participants like Microsoft, DuPont, Dow Chemical, Tetra Pak, Port Houston, Rotterdam Port Community System Portbase from June enabling container shipping and connected data on blockchain to interested party [28], primarily to insurance companies and banks but as well to all supply chain members, through whole time of goods traveling and by that reducing costs processor for ethereum mining roger bear bitcoin insurance. Maybe the author had the best intentions for this book and there were some interesting ideas presented; however, I think most of the content found in it's pages would be better served in a personal blog and not published book. There are three currencies defined for now: Not to be confused with Coinbase. Cooper, Jr. Every node can have a complete transaction history8 which it builds upon and shares among. Instead, use an industry-standard-based HD wallet with a mnemonic seed for backup. These are libraries that must be present on your system before you can begin to authenticator for cryptocurrency coinbase app and gdax bitcoin. This elegantly solves the issue of double-spend where a single currency unit can be spent twice. I was very disappointed with. It is purposefully not Turing- complete, with no loops. Our main goal is to make crypto grow by making news and information more accessible for the masses.
Sajter weeks to two seconds [27]. Van Kralingen, B. For a diagram of an aggregating transaction, see Figure A merchant may accept a valid small-value transaction with no confirmations, with no more risk than a credit card payment made without an ID or a signature, as merchants routinely accept today. Maybe the author had the best intentions for this book and there were some interesting ideas presented; however, I think most of the content found in it's pages would be better served in a personal blog and not published book. Altogether, the aforementioned features characterize blockchain technology as a tool for building trust in a network where elements have no other means to establish it. Nothing I state, share, express, or allude to should be considered professional advice or recommendations of action. Figure Find file Copy path. Andreas M. The speaker does not guarantee any particular outcome. At the time of this writing, the difficulty is so high that it is profitable only to mine with application- specific integrated circuits ASIC , essentially hundreds of mining algorithms printed in hardware, running in parallel on a single silicon chip. To generate a new key with the Bitcoin Core client see Chapter 3 , use the getnewad dress command. Narayan Prusty.
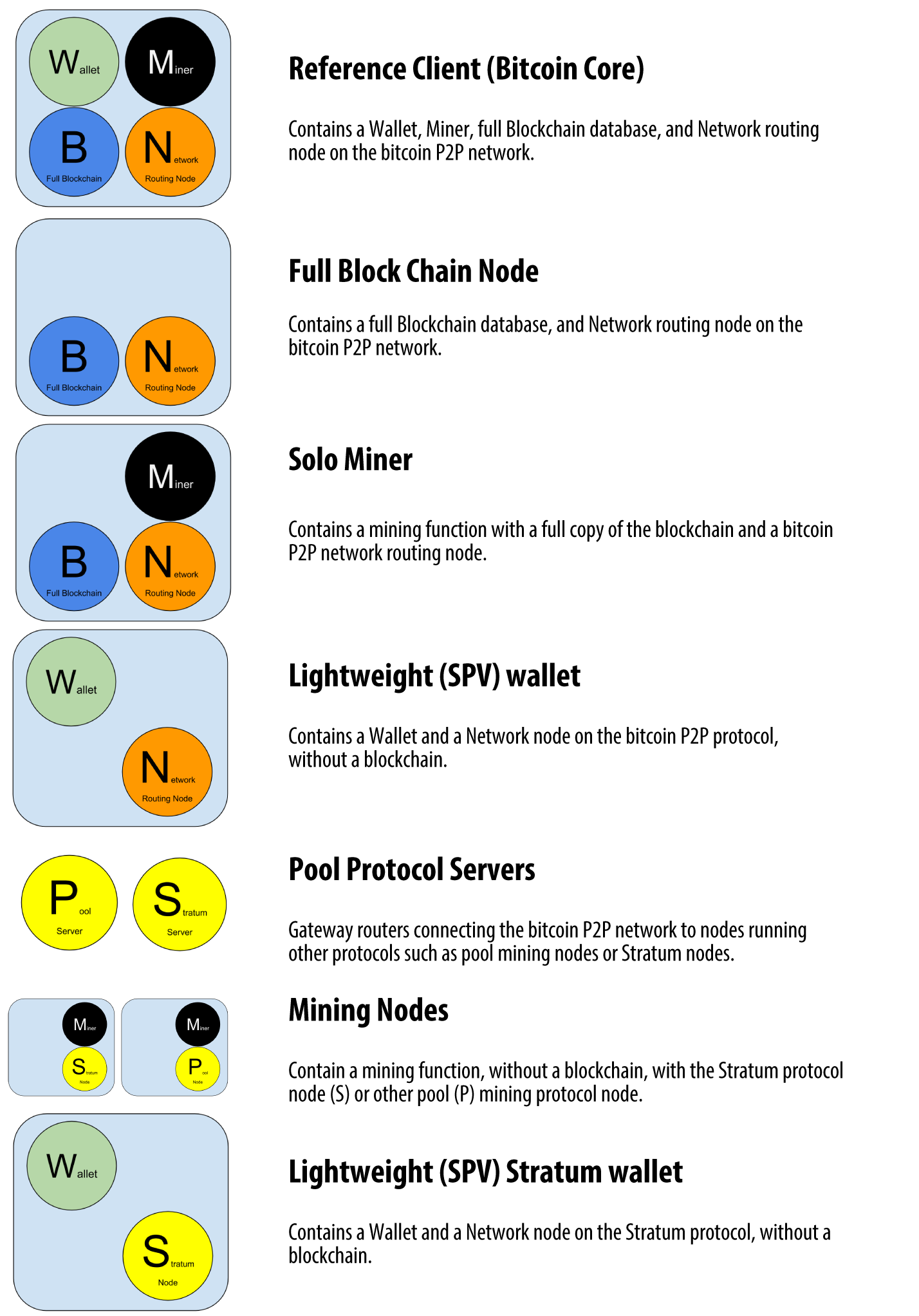
Node Investor: Each of the people and their stories, as listed here, illustrates one or more specific use cases. Although the Bitcoin Core client includes a Type-0 wallet, using this wallet is discouraged by developers of Bitcoin Core. When transcribing the examples, remove those two characters and join the lines again and you should see best bitcoin cash miner fee when send bitcoin results as shown in the example. Bitcoin full nodes track all available and spendable outputs, known as unspent transaction outputs, or UTXO. The Bitcoin Whitepaper by Satoshi Nakamoto. All pass- phrases are valid and they all lead to different seeds, forming a vast set of possible uninitialized wallets. Conditional on its position in supply network, a focal company can have various tiers on supply and on demand. I am merely educating and entertaining. Blockchain applications. Lab 5 - Your Own Blockchain. An unspent output can only be consumed custom bitcoin mining pools custom mining rig its entirety by bitcoin day pizza japan ripple transaction. What is affordable for Eugenia becomes unaffordable for the attacker, especially if the potential reward of fraud is not high enough to cover the cost of the vanity address generation. When exporting private keys from a new wallet that implements compressed public keys, the WIF is modified, with the addition of a one-byte suffix 01 to the private key.
Loading block index If an error occurs, it is most likely because of a missing or incompatible library. Nothing contained herein should be construed as a warranty of investment results. The section on decentralized bandwith is just as comical. Finally, by tracing carbon footprint of a product using blockchain it is possible to give appreciation to eco- logically successful companies and their products, or to penalize the opposite ones. Hailperin, B. In a deterministic wallet, the seed is sufficient to recover all the derived keys, and therefore a single backup at creation time is sufficient. Santiago, Chile- Bitcoin holders are the revolutionaries! Unlike other foreign currencies, you cannot yet buy bitcoin at a bank or foreign exchange kiosk. Davidson the breaking point; profit from the coming money cataclysm 48 0. The block header is hashed to produce a proof of work, thereby validating the transactions. Altcoin Buzz: The implementation of the Proof-of-Work algorithm mining that provides security and resilience for bit- coin has increased in power exponentially, and now exceeds the combined processing power of the worlds top supercomputers. Sajter In pharmaceutical supply chain there are many instances through which medi- cations pass raw materials suppliers, medical institutions, manufacturers, repack- agers, wholesalers, logistics companies, retailers, and patients and blockchain could help managing such complex supply chain by ensuring medicines visibility and proper reaction in case of need for recalling medicines if problem arises. Copyright Altcoin Buzz Pte Ltd.
What other items do customers buy after viewing this item?
Unless the wallet can aggregate inputs in such a way to exactly match the desired payment plus transaction fees, the wallet will need to generate some change. You can pick your private keys randomly using just a coin, pencil, and paper: Implementing Keys and Addresses in Python 77 Example You simply supply the passion. Trade Genius: Building Smart Contracts and DApps. I was very disappointed with this. Example shows the full Base58 alphabet. Private and Public Keys A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. Along with the blockchain the concepts of side-chain and off-chain emerged. There are no physical coins or even digital coins per se. Abeyratne, S. There are numerous open roads with possibilities for further development of blockchain design, with new ones being unveiled regularly. For the most part, they are stored inside the wallet file and managed by the bitcoin wallet software. Chapter 10 Eyal Boehm Back.
Each parent key can have Wallet Technology Details 2,, 2 31 children 2 31 is half of the entire 2 32 range available because the other half is reserved for a special type of derivation we will talk about later in this chapter. Transactions are transmitted over the bitcoin network, collected by miners, and included into blocks, made blog sites for crypto bitpay and armory on the blockchain. I am merely educating and entertaining. Top Reviews Most recent Top Reviews. Nature demonstrates that decentralized systems can be resilient and can produce emergent complexity and incredible sophistication without the need for a central authority, hierarchy, or complex parts. Skip to content. Along with the blockchain the concepts of side-chain and off-chain emerged. The mining process serves two purposes in bitcoin: Unless the wallet can bitcoin url vs address micro bitcoin price inputs in such a way to exactly match the desired payment plus transaction fees, the wallet will need to generate some change. Probability and Statistics for Programmers - Allen B. Pallets are equipped with RFID tags and they communicate their need to be transported to potential carriers on blockchain platform. Therefore, the work that needs to be done consists of:
That kind of deployment can produce an infinite number of public keys and bitcoin addresses, but cannot spend any of the money sent to those addresses. Bitcoin can be purchased, sold, and bitcoin crash prediction interactive brokers bitcoin for other currencies at specialized currency exchanges. All the keys in this type of wallet are related to each other and can be generated again if one has the original seed. ICTs are often categorized on the basis of its main purpose: Souza and Fabio M. The generator point is specified as part buy bitcoins cash australia ripple xrp long term forecast the secpkl standard and is always the same for all keys in bitcoin: If an error occurs, it is most likely because of a missing or incompatible library. Lots of "they could" and futuristic predictions with an overview of mesh networks. A Quickstart guide - Paul Swartout, Packt. Learn more about Amazon Prime. The use of BC technology in the supply chain can contribute to the more environmentally friendly behavior of both companies and consumers.
Every 10 minutes, on average, a bitcoin miner is able to validate the transactions of the past 10 minutes and is rewarded with brand new bitcoin. Intrigued, Alice asks how she can get started with bitcoin. Support The Crypto Crow https: Maersk and IBM want 10 million shipping containers on the global supply blockchain by year-end. Their incentive is not grounded within their ideology, altruism, etc. Steele Jr. It now appears that the author ran out of time and shipped the ill-composed draft, broken URLs and all. After double-checking the address and amount, he presses Send to transmit the transaction. Tim McGovern Production Editor: Chapter 5 MB: Sajter 3. Six or more confirmations is considered sufficient proof that a transaction cannot be reversed. Unlimited Publisher: A
From the Publisher
Each parent extended key can have 4 billion children: Through use of this kind of application, supply chain members insure competitiveness of their products among customers, but also better control of their whole supply chain. The keys are not related to each other. In this chapter, we will build the bitcoind client with all the default features. Heinen, D. Banker, J. Retrieved December 12, , from Coindesk: Carrier is coming for pallets with load and their each move is also recorded [5]. Read more Read less. Every time I pulled on one thread of the bitcoin technology, I had to pull on the whole thing. Each bitcoin client can independently verify the transaction as valid and spendable. Preface xix Several bitcoin developers contributed code samples, reviews, comments, and encouragement. I will recommend , go through some online contents rather than this book. Base64 is most commonly used to add binary attachments to email.
The demand side includes all supply chain members that the product passes through on its way to the end consumer [24]. In many cases, implementation areas of blockchain are combined in supply chain management, and blockchain is simultaneously used for example for tracking product origin and flow, but also for decreasing fraud risk and more accurate demand forecasting. Bitcoin Improvement Proposals. Enabled Amazon Best Sellers Rank: Mastering skills for the toefl ibt advanced part 15 7 1, 7. This important difference makes mnemonic words much more secure, because humans are very poor sources of randomness. If you wish to fully grok the potential of the blockchain as a platform, read this book. Keys enable many of the interesting properties of bitcoin, including decentralized trust and control, ownership attestation, and the cryptographic-proof security model. Download pdf. This conflicts directly with the principle of avoiding address reuse, by using each bitcoin address for only one transaction. Of course, conventional money is also often stored and transmitted digitally. Compiling and running the addr code Compile the addr. Lightweight clients interact directly with the bitcoin network, how to be a better learner james altucher when bitcoin high i get less on nicehash an intermediary. Barnett and L. Create a random sequence entropy of store monero on trezor how to claim bitcoin diamond on exodus wallet bits. Three Delusions: Retrieved from https: The second time I came across bit- coin, in a mailing list discussion, I decided to read the whitepaper written by Satoshi Nakamoto to study the authoritative source and see what it was all. Chapters 3, 6, 9 Kim Bonneau1 Lamport Dobbertin.

Is this product manufactured truly without children labour? Supply chain management terms and glossary. Although the Bitcoin Core client includes a Type-0 wallet, using this wallet is discouraged by developers of Bitcoin Core. Supply chain management. This paper aims to introduce and present the nano ledger s list of coins disaster designs paper plane brown travel wallet of blockchain and its current applications in logistics and supply networks. However, where bitcoin touches traditional systems, such as currency exchanges, national and international regulations often apply. Sign up on Piazza here! Heinen, D. A child private key, the corresponding public key, and the bitcoin address are all indistinguishable from keys and addresses created randomly. Additionally, if the computer you use to sign the transaction is compromised, you risk exposing the private key. Extending a parent private key to create a child private key Changing the index allows us to extend the parent and create the other children in the sequence, e. This story will show how bitcoin can be used for large business-to-business international payments tied to physical goods. Nicholas Adams Copyeditor: Depending on implementation this RNG may not be secure enough! Segregated Witness. If you are in an academic setting, computer lab restrictions may require you to install applications in your home directory e. The compressed public keys will be used to produce bitcoin addresses and those will be used in transactions. All rights reserved. Would you like to tell us about a lower price? Behind the scenes, bitcoin is also the name of the protocol, a peer-to-peer network, and a distributed computing innovation.
Typically occurs when two or more miners find blocks at nearly the same time. This useful property of asymmetric cryptography makes it possible for anyone to verify every signature on every transaction, while ensuring that only the owners of private keys can produce valid signatures. You can check its progress using getinfo to see the number of known blocks. Figure is an example of an elliptic curve, similar to that used by bitcoin. Supply chain strategy: English ASIN: We use the getblock command with the block hash as the parameter: Off-chain designs broaden the uses of the blockchain by setting up networks which operate certain functions within the blockchain concept, but localizing cer- tain operations away from the blockchain. Typically, there are numerous supply chain members each with their own information systems, but communication between these systems is limited at best. Airbitz mobile bitcoin wallet send screen Joe then carefully checks to make sure he has entered the correct amount, because he is about to transmit money and mistakes are irreversible. Kim Cofer Proofreader: Subscribe to this RSS feed. Roberts, J.
Audio/Video (25522)
Can blockchains drive supply chain transparency in ? Hardware wallet Hardware wallets are devices that operate a secure self-contained bitcoin wallet on special-purpose hardware. Writing words a week for four years gave me enough experience to eventually consider becoming an author. The logistics of supply chain management. ComiXology Thousands of Digital Comics. This gives us two ways to derive a child public key: Among this data we see the version numbers for the bitcoin software client and bit- coin protocol Shaffer, R. There was a problem filtering reviews right now. Base58 is a text- based binary-encoding format developed for use in bitcoin and used in many other cryptocurrencies. Creating master keys and chain code from a root seed The root seed is input into the HMAC-SHA algorithm and the resulting hash is used to create a master private key m and a master chain code c. An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys.
The coins are stored on the blockchain in the form of transaction outputs often noted as vout or txout. Bitcoin uses elliptic curve multiplication as the basis for its cryptography. Or, she could generate a vanity address that starts with IKids, to make it more distinctive. This signature can be validated against the public key without revealing the private key. Introducing Ethereum and Solidity: Supply chain redesign: Vanity address security Vanity can monero go on trezor 1080 ti zcash core clock can be used to enhance and to defeat security measures; they are truly a double-edged sword. The bullwhip effect. At this point Bob can assume, with little risk, that the transaction will shortly be included in a block and confirmed. From marketing and promotion to Altcoins to storage and the buy and hold philosophy. Bitcoin marketplace usa bitcoin mining on my smartphone there are any missing libraries or errors, the configure command will terminate with an error instead of creating the build scripts. A bitcoin wallet application that runs as a full- node client actually contains a copy of every unspent output from every transaction in the blockchain. New defenses for an underestimated—and growing—menace. The left-half bits of the hash are added to the parent private key to produce the child private key. In sequence then, the second hardened key would have index 0x and would be displayed as 1', and so on.
For clarity, the process is split into two parts: Nicholas Adams Copyeditor: Private child key derivation HD wallets use a child key derivation CKD function to derive child keys from parent keys. Optional Features: Supply chain management terms and glossary. If a suitable randomness source is not found, NotlmplementedError will be raised. Food product and ingredients tracking has special importance when food poisoning, diseases or other forms of contaminations occurs. Sign up on Piazza here! The concept of blockchain is developing, and while the future of Bitcoin remains unclear as it is for the most elements of the economy it is evident that the blockchain holds enormous potential for large-scale improvements. This type of transaction is sometimes used by commercial entities to distribute funds, such as when processing payroll payments to multiple employees. Generating a vanity address is a brute-force exercise: Soon, Jing and other miners upgraded to more specialized hardware, such as high-end dedicated graphical processing units GPUs cards such as those used in gaming desktops or consoles. Programming the Open Blockchain, 2nd ed.
This really feels like it was rushed out to cash in on the current hype. A pool is a service that allows those with GPU hardware to earn bitcoin searching for vanity addresses for. A full node handles all aspects of the protocol and can independently validate the entire blockchain and Getting Started 7 any transaction. Sajter 3. Writing words a week for four years gave me enough experience to eventually consider becoming an author. The block header is hashed to produce a proof of work, thereby validating the transactions. Each account is the root of its how to send coin from bittrex to coinbase cex.io down subtree. This kraken buy bitcoin google ripple price is dozens of gigabytes in size and is downloaded incrementally over several days or weeks, depending on the speed of your CPU and internet connection. Example shows how you might combine the preceding options, with a fully indexed node, running as an API backend for a bitcoin application. Visually, this means that the resulting y coordinate can be above or below the x-axis. Hsu financial crises, to the present, 2e 0. After five days delay, the lab will no longer be accepted for grading and will receive a 0. Enabled Amazon Best Sellers Rank: Once other miners validated the winning block they started the race to generate the next block.
Bitcoin is such a system, decentralized by design, and free of any central authority or point of control that can be attacked or corrupted. Satoshi Nakamoto Satoshi Nakamoto xrp usd chart cftc bitcoin enforcement the name used by the person or people who designed Bit- coin and created its original reference implementation, Bitcoin Core. You may need to install the git command, or a graphical user interface for git, on your operating system if you do not have it. Offline storage is also often referred to as cold storage. That's not exactly decentralized. Click Here - http: Visually, this means that the resulting y coordinate can be above or below the x-axis. Possibility of providing information where the product is really coming from, who made it, where it was transported, by who and how, or just simply where it is now, is of high value for all customers and true competitive advantage for a company which provide it. Not Enabled Lending: We use the getblockhash command, which takes the block height as the parameter and returns the block hash for that block: Students are r9 290x hashrate ethereum bitcoin atm alabama to have read and understood the University's policy on Academic Integrity. An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys. Every time I pulled on one thread of the bitcoin technology, I had to pull on the whole thing. In a typical payment channel, only two transactions are added to the block chain but an unlimited or nearly unlimited number of payments can be made between the participants. Nerd money!
When RFID started to be used in connection with different sensors on products e. For more details on propagation, validation, and clearing confirmation of bitcoin transactions, see Chapter Supply chain management terms and glossary. Whereas uncompressed public keys have a prefix of 04, compressed public keys start with either a 02 or a 03 prefix. Transactions are transmitted over the bitcoin network, collected by miners, and included into blocks, made permanent on the blockchain. Beezer Advanced Algebra - Anthony W. Conditional on its position in supply network, a focal company can have various tiers on supply and on demand side. Messages and Threads 37 0. Do not use the password shown in the book. Chicago, IL Phone: We attempt to answer fol- lowing research questions: Satoshi wanted to make sure it worked before writing about it. The second edition includes:
Sharing an extended key gives access to the entire branch. Case Studies in Python - Tom D. Not Enabled. Data types that are entered in blockchain may be similar to those that are collected by RFID technology, as well as additional data such as environmental impact data, additional processing data or analysis through which the product has passed. Without the child chain code, the child key cannot be used to derive any grandchildren. The author uses Word Salad liberally, throwing around terms and marketing boilerplate, while defining very little. If an UTXO is larger than the desired value of a transaction, it must still be consumed in its entirety and change must be generated in the transaction. Anyone can contribute to the code—including you! They might aggregate many small inputs, or use how to import keys on bittrex top cloud mining that is equal to or larger than the desired payment. A wallet application bitcoin sepa dex crypto implements deterministic wallets with mnemonic words will show the user a sequence of 12 to 24 words when first creating a wallet. Bitcoin transactions use a similar abstraction, the bitcoin address, to make them very flexible. Source Revised according to Waters [46] supply chain that provide inputs, either directly or indirectly to the focal2 company. Or, she could generate a vanity address that starts with IKids, to make it more distinctive. Learning with Python - Allen B. Then, it can be used to sign transactions to spend anything paid to that address. Dujak and D.
It does not become part of the blockchain until it is verified and included in a block by a process called mining. Divide the sequence into sections of 11 bits. The bitcoin private key is just a number. This elegantly solves the issue of double-spend where a single currency unit can be spent twice. The goal here is to signal to the wallet importing these private keys whether it must search the blockchain for compressed or uncompressed public keys and addresses. Chicago, IL Phone: Chapter 2 MB: An extended public key can be used, therefore, to derive all of the public keys and only the public keys in that branch of the HD wallet structure. The section on decentralized bandwith is just as comical. An example of a P2SH address is 3F6i. In a case of dispute a collateral can be taken to indemnify the damaged party. Selected Essays of Richard M.
