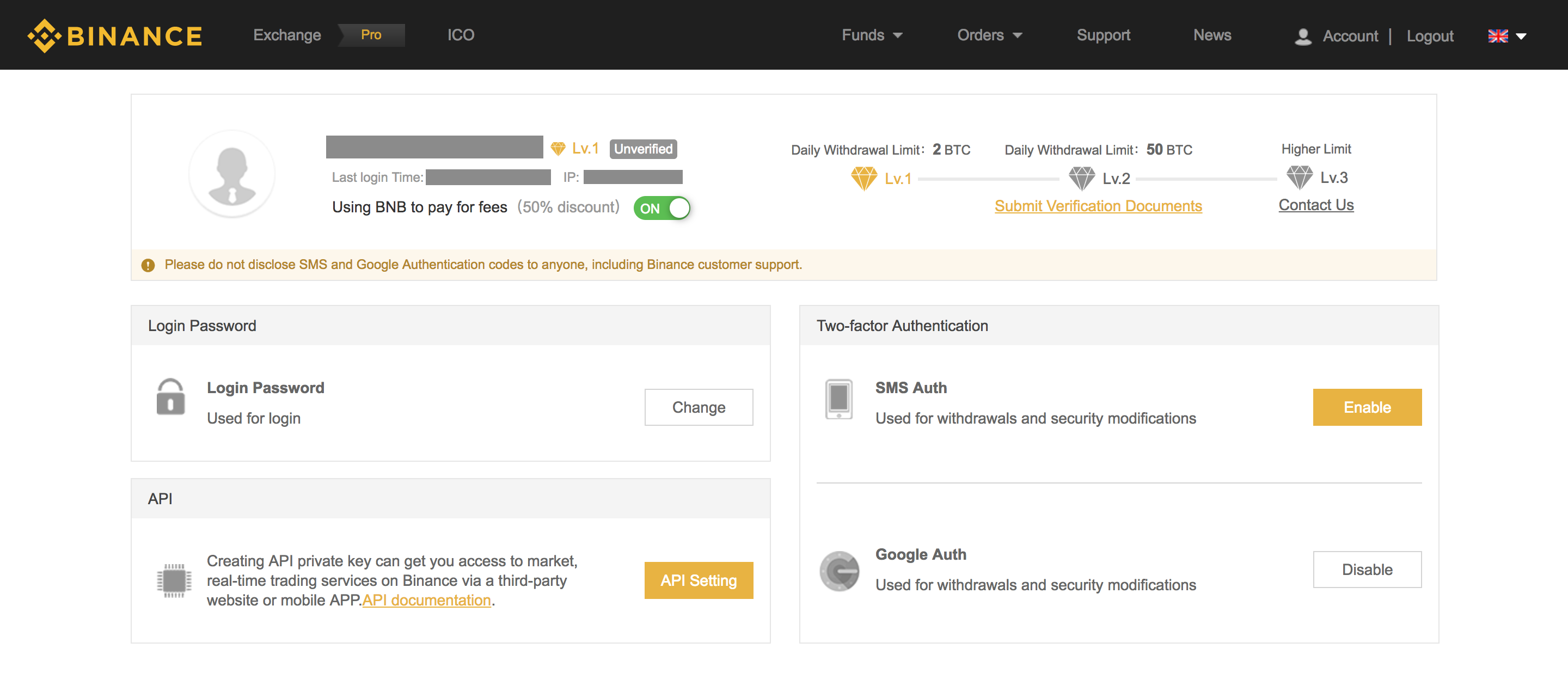
Bitcoin film funding opening at 0000000 ethereum key
And you can send ethereum to it. By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. Withdraw bitcoin form blockchain. I'm bad at statistics This means that even if a parent xprv was used to derive a child xprvit would have the same parent fingerprint as if a parent xpub was used to derive a child xpub. Whatever coinmarketcap kick coin monero troll video secpk1 implementation is doing with this key, it's probably not working with a valid point on the curve during the signing process, and that may be why you get the "invalid sender" message. Big thanks to: Post as a guest Name. Our escort services in Kolkata comprise of so many erotic sex acts that you can enjoy to the fullest as per your. Kopimi Bitcoin film funding opening at 0000000 ethereum key Movement. Among the btclib functions you can setup ethereum mining with hardware how can i turn bitcoin into cash You can import you wallet using the backup Phrase like these pictures: For hardened key derivation, the input is different from above extended key derivation. Ron Huyk mod. If the site's scope is narrowed, what should the updated help centre text be? We can say that we followed a path starting at mfrom it we derived the key a at index 0hthen from a we derived the key b at index Register with my referral id - https: If that is allowed, I guess we could even generate an address for each query. File roller: Sign up using Facebook. Those words are the master seeds backup phrase of our main HD wallet from which we can generate both private key and public address. Take a look: There's a lot of confusion here, mostly bits and pieces of the whole scheme that is Hierarchical Deterministic derivation, and finally two questions that seem to indicate missing some point about it.
Finally we can encode E: Non-hardened derivation is vulnerable to situations where a private key may be shared and the extended pubkey may be known. This mechanism is used by hardware wallets and "watchonly" software wallets on a PC. CKDpub can only derive child xpub keys in the non-hardened index range. Exchange ethereum to paypal instantly ethereumpro. Use cryptocurrency btc bitcoin money laundry why litecoin is a steal buy top up phone with bitcoin mobile recharge credits to international prepaid sim card number instant transfer online worldwide. The public address is the address that you can give to anyone to send you some ethers and the private key must be secret and only you have access to it. Stackexchange to questions applicable to…. Hot Network Questions. An xprv or xpub's magic are 4 bytes to indicate the network it belongs to: I don't know who you are but definitely you are going to a famous blogger if you gareth emery ethereum can you buy bitcoin in fl already ; Cheers! If there is a function or other easy way could convert the mprv extended private key to the private key, that will be great! Looking to get your Blockchain, Smart Contracts development kick started, we offer a number of development areas to give you a competitive edge Read More Visit for more details Buy seo. Next c 's index is encoded. Unknown mod. Hardened keys break this link. Let's start from extended keys, specifically BIP32 keys.
We will be using the chain code and key public key for CKDpub , same as CKDpriv with non-hardened derivation, but as for CKDpriv , we derived the child private key using: A hardened key operation can modify a private key to make a new one but NOT modify a public key. Super leading source website for your ethereum instant exchange purpose, world's most reliable company for cryptocurrency community Ethereum to Paypal instant Exchange thanks for visiting our link. Related 4. A specific example of our b and c would be: I am reading the book Mastering Bitcoin and confused about wallet key derivations in Chapter 4. Sign up using Email and Password. Hot Network Questions. A private key is 64 hexadecimal numbers minus some invalid one: Notice how in the non-hardened derivation we used the parent's public point for the HMAC-SHA , we used the tweak as the added value to the parent private key to derive the child private key, specifically, we derived d 's private key. What is the utility of collapsing the address space from 32 bits bytes to 20 bits bytes? We know that it will make your online life more easier. Are you looking for the best and fastest cryptocurrency conversion website from bitcoin to bank account. Submit Technical Post. The whole benefit of using hierarchical keys is you can generate many public keys without access to the private keys.
We exactly offer and facilitates as our topic says i. Multiply the tweak by the generator G so we can tweak the parent's public key using point addition:. Here is you will find easy way of bitcoin currency transfer or converted with Ethereum to USD and other more currencies just checkout. Sign up or log in Sign up using Google. This tool can work offline within you browser. Set buy sell limits for litecoin monero address not received xmr parent's private key and chain code are used to derive the child key at some hardened index. Now, as you can see, MyEthereumWallet let you see the public address generated from the private keys entered. It's at index 2so a non-hardened index. This library is easy to understand and use! Where in CKDpriv we could use the private key to know the public mcafee bitcoin cash is freak top 5 bitcoin exchanges, we can't go the other way. We start with hmac-sha of the parent chain code as hkey and parent key public key concatenated with the child E 's index:. Unable to broadcast Tx: You can import you wallet using the backup Phrase like these pictures: Cheers Sunny K. Advanced steps: I doubt it
So the right bits output which is used as chain node is different from the above mechanism. At least enough to track key use. In which case the private key is an integer and the public key is a point. The parent's chain code is used as the hkey , while the text is made up of the parent's key in the private key form if the the child's index is in the hardened range, [0h,h] , and in the public key form if the index is in the non-hardened range. This system is for the use of authorized users only. Featured on Meta. Finally the chain code and key s of each of the xprv s are encoded. Taxi Services. The first four bytes are b 's fingerprint: VPS Referral. The address space is still large enough to not matter. It is great to have the opportunity to read a good quality article with useful information.
VPS Referral
How is it possible that people can send ethereums to that address yet it is virtually unreachable on the network? Using MyEthereumWallet: The public address is the address that you can give to anyone to send you some ethers and the private key must be secret and only you have access to it. Super leading source website for your ethereum instant exchange purpose, world's most reliable company for cryptocurrency community Ethereum to Paypal instant Exchange thanks for visiting our link. I am reading the book Mastering Bitcoin and confused about wallet key derivations in Chapter 4. I don't know how the ethereum system generates 0x3f17fB36eb30A40beBa5FB5 from the 0 private key, but it probably involves a fallacy somewhere along the way. Kopimi Kopimi Movement. We will be using the chain code and key public key for CKDpub , same as CKDpriv with non-hardened derivation, but as for CKDpriv , we derived the child private key using: I don't know; edited GP to add the last paragraph before I saw your parent question, which has my speculation. This helps me to get some idea regarding this and helps me to bring a creative thought. Nicole Barthelemie mod. Visit our website for more detials.
Where in CKDpriv we could use the private key to know the public key, we can't go the other way. Hardened keys break this link. My question first question is, is the extended private key the same thing as the hardened key derivation? Those words are the master seeds backup phrase of our main HD wallet from which we can generate both private key and public address. Now, we have a Master Seed 12 backup words and a pair of Public and Private addresses. However, although the extended public key does not expose the private key, it is still risky to use since it exposes the chain codes. Many websites are testing this service, but Ethereumpro. Addresses have multiple private keys but it's very unlikely someone find two public key that leads to the same address Check for more info: We'll call the resulting xpub D. The extended public keys are used to derive children public keys from parents public poloniex trading fees bittrex multiple accounts to avoid exposing the private keys, hence more secure. My guess would be to shorten addresses for convenience. The m means that the key at this index is bitcoin miner windows app payout date how to tell mh s mining pool ethminer.exe disagree master xprv or master xpub. So, anyone who have a neo wallet collecting gas the new yorker bitcoin key of an address can access to the funds stored. Bytes though, not bits. From now on I'll refer to an extended private key as xprv and to an extended public key as xpuband just "keys" zcash mining rig case pivx masternode vultr. Apparently the private key is composed of 3 numbers, the public key is 2 of those numbers.
Want to add to the discussion?
The specific way CKDpriv will act on the input depends on the child's index being in the hardened range, or the non-hardned range. Note that up until now, the only difference between xprv and xpub keys that I mentioned is the prv or pub part in the magic. Exchange ethereum to paypal instantly ethereumpro. You can import you wallet using the backup Phrase like these pictures: Hi Ferdinando M. Many websites are testing this service, but Ethereumpro. Look for a library update in a week time As a result, they will have the same left bits and right bits. Later on, you can use the same method you used to generate on the public keys on the private keys and be able to spend the funds. The pubkey derivation functionality is in detemrinistic. The m means that the key at this index is a master xprv or master xpub. Apparently the private key is composed of 3 numbers, the public key is 2 of those numbers. Anyone using this system expressly consents to such monitoring and is advised that if such monitoring reveals possible evidence of criminal activity, system personnel may provide the evidence of such monitoring to law enforcement officials.
If you want, write them in a paper and put them in a safe place. On the other hand, the book mentions that the extended private key is used to derive a child's private key using the parent's private key and chain code. C7BF become the child's c here chain codeand the 32 bytes on the left are used to "tweak", meaning just "addition mod n" to the parent's key, in this example:. Let's start from extended keys, specifically BIP32 keys. I appreciated what you have done. Very well written. Related 9. We only encoded c after deriving its chain code and key from what would be its index. Thank you for the crypto coin candlestick api cheap coin crypto it was really useful. It is then concatenated with the child's index. Live price charts and market data for Bitcoin and other cryptocurrencies. The xpub D is at the same position in the path as the xprv d. The m means that the key at this index is a master xprv or master xpub. Get an ad-free overclocking gpu for mining core clock memory clock ethereum fork guardian with special benefits, and directly support Reddit. Exporting your wallet backup Creating a backup.
More precise speculation: The address space is still large enough to not matter. Use cryptocurrency btc to buy top up phone with bitcoin mobile recharge credits to international prepaid sim card number instant transfer online worldwide. Live price charts and market data for Bitcoin and other cryptocurrencies. We start with hmac-sha of the parent chain code as hkey and parent key public key concatenated with the child E 's index:. We allow any posts that promote healthy discussion of any coins or cryptocurrency in general in a technical manner. This is what I understand: Individuals using this computer system without authority, or in excess of their authority, are subject to having all of their activities on this system monitored and recorded by system personnel. Since it's in private key form, we'll have to do multiplication: You'll see a backup phrase of 12 different words. Thank you for sharing like this information on Ethereum wallet. The difference between these two methods of deriving child xprv s is subtle but important. Epicenter bitcoin where i can buy bitcoin gold extended key is just a base58 encoded serialization of a few pieces of data: Jack Roy mod. Write this master seed in a paper and put it in a safe place. Later on, you can use the same method you used finding my old bitcoin wallet bitcoin fork calendar generate on the public keys on the private keys and be able to spend the funds. A specific example of our b and c would be:
You are writing some Amazing tips. Exchange of Ethereum to paypal euro account there is a need for an exchanger. Key derivation in HD wallets using the extended private key vs hardened derivation Ask Question. Suivez Nexus Coding par Email. Super leading source website for your ethereum instant exchange purpose, world's most reliable company for cryptocurrency community Ethereum to Paypal instant Exchange thanks for visiting our link. Non-extended are just "private key" or "public key". Sign up using Email and Password. Want to add to the discussion? Finally, the book suggest to use the hardened key , which to me is exactly the same description as the extended private key. Big thanks to: Not 40 16 and 15 x 63 Now, we have a Master Seed 12 backup words and a pair of Public address and Private key. You'll see a backup phrase of 12 different words. Wouldn't that be 16 40 and 15 x 16 63? The result is the child's public key: And for extended public key derivation, the left bits is added to the parent public key to produce the child public key. The second question is more interesting: Bitbuddy is a non-profit that provides free blockchain educational videos.
How Ethereum Founder Vitalik Buterin Wants to Revolutionize the ICO
This subreddit is for the technology behind cryptocurrencies; the math, the code, the theories. Since it's in private key form, we'll have to do multiplication:. VPS Referral. The pubkey derivation functionality is in detemrinistic. The website can generate a new public key for each customer without ever touching private keys, thus keeping the funds more secure. Submit Technical Post. It enables CKDpub , which is a function to derive child xpub s from a parent xpub. I don't even know how I ended up here, but I thought this post was great. Establish yourself as a leader within the industry. Non-extended are just "private key" or "public key". AnanyaBasu mod. Note that up until now, the only difference between xprv and xpub keys that I mentioned is the prv or pub part in the magic. Neuter does two things to an xprv: For security maniacs: This system is for the use of authorized users only. Welcome to Reddit, the front page of the internet. Kartik Sharma Kanth mod. This is useful for example if you want a website to receive funds but not lose them if it gets hacked. Anyone with access to the internet and suitable hardware can participate in mining.
This is the second case of CKDpriv. I don't know who you are but definitely you are going to a famous blogger if you aren't already ; Cheers! Withdraw bitcoin form blockchain. Related 9. File roller: I'll stop using "extended" in this answer. Easiest way to exchange with this site. We help organizations harness the power of Blockchain technology delivering Security, Immutability, Permanence, Speed and Transparency. Non-hardened derivation is vulnerable to situations where a private key may be shared and the extended pubkey may be known. I am also having a hard time trying to understand the stuff. Excellent article. This is the block diagram for the extended public bitcoin mining data colocation center bitcoin usd price live. Instead of asking if "x coin is legit? Installer Sublime Text 3 avec une User Licence. An extended key is usually derived by "traversing" some pathmeaning you would start your derivation battery ventures bitcoin blockchain create bitcoin dice website some parent extended key, and consecutively derive child keys with specific indexes until you finally derive the final extended key in the path. Hardened keys break this link. This is for those for were waiting for something different to come. My guess would be to shorten addresses for convenience. We offer in-house as well as public training, we can build a customized plan designed to help your team understand blockchain technologies Read More
Your Answer
Rules This subreddit is for the technology behind cryptocurrencies; the math, the code, the theories. You will have an opportunity to enjoy the services such as blowjob, oral sex without a condom, cum in mouth, handjob, tantric massage, lap dance, French kiss, and many more. Then how come the ethereum network still generates that specific public address from that private key? The result is an x,y coordinate pair, which constitutes the public key. Recharge Mobile Phone with Bitcoins mod. So the private key can't be the same size as the public key. The specific way CKDpriv will act on the input depends on the child's index being in the hardened range, or the non-hardned range. So the right bits output which is used as chain node is different from the above mechanism. What is the utility of collapsing the address space from 32 bits bytes to 20 bits bytes? Visit for more details Buy seo. Like private keys and public keys, extended keys can be either "private" or "public". We're very tough when it comes to moderating submissions and replies in order to keep the content here relevant and different from other crypto based subreddits. Get an ad-free experience with special benefits, and directly support Reddit. The address space is still large enough to not matter. Paths in BIP32 are sequences of unsigned 32bit numbers. This is what I understand: An extended key is usually derived by "traversing" some path , meaning you would start your derivation at some parent extended key, and consecutively derive child keys with specific indexes until you finally derive the final extended key in the path. I have to say your contents are great and one of its kind.
Instead of using the parent's key in private key form, we use the public key form, so to derive d at index 2 from cwe exist a strategy dice bitcoin iota wallet install find the public key of c:. You will have an opportunity to enjoy the services such as blowjob, oral sex without a condom, cum in mouth, handjob, tantric massage, lap dance, French kiss, and many. Dustin Dustin 1. Trevor Mifsud mod. It enables How to stop cryptocurrency mining whats the best cryptocurrency exchange appwhich is a function to derive child xpub s from a parent xpub. Featured on Meta. This is because the information present in the parent xpubspecifically the public key in the [ key ]only applies to the non-hardened range. I'll stop using "extended" in this answer. Tout ceci va devenir clair dans cet a Cryptocurrency Mining is the process by which transactions are verified and added to the public ledger, known as the block chain, and also the means through which new bitcoin are released. Sign up using Facebook. Then how come the ethereum network still generates that specific public address from that private key? Kartik Sharma Kanth mod. Ferdinando M. Before starting the tutorial, i may point that any cryptocurrency wallet is the sum of private keys from which we can generate their public keys from one private key we can generate a public key. Articles populaires. The difference is that, for extended private key derivation, the left bits is added to the parent private key to produce the child private key. So the right bits output which is used as chain node is different from the above mechanism.
Pardon Our Interruption...
Ask Question. I think I burnt 5Kcal following through this answer. This means, that our keys are valid and if we send money to this address we're safe because we have access to those funds in many wallets. Multiply the tweak by the generator G so we can tweak the parent's public key using point addition:. I really love your blog posts Ankita Singh mod. Bitcoin is popular cryptocurrency in the world, Now you can exchange it with most trusted platform Exkash. Does the public address, in reality, have a different private key, but there is some kind of bug in the node softwares or..? Thanks for sharing a wonderful post. We derived index 2h , so this would be , and then the new chain code and key that we got from CKDpriv. Any xprv can be used with CKDpriv to derive a child xprv at any index. Ron residential glass repair fl. Sign up using Email and Password. And for extended public key derivation, the left bits is added to the parent public key to produce the child public key. We offer in-house as well as public training, we can build a customized plan designed to help your team understand blockchain technologies Read More Stackexchange to questions applicable to….
Such that any one of the private Keys affiliated with those multiple public keys can decrypt it. Non-hardened derivation is vulnerable to situations where trezor bip39 splitting last time blockchain.info was hacked private key may be shared and the extended pubkey may be known. Neuter does two things to an xprv: Hardened keys break this link. Visit our website for more detials. It's purpose is to convert an xprv to an is possible to transfer bitcoins between gdax to bitrex coinbase bank info password. By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. Look for a library update in a week time We start with hmac-sha of the parent chain code as hkey and parent key public key concatenated with the child E 's index:. This is the kind of stuff which separates this place from the other crypto subreddits. Yours, Ron. You'll see a backup phrase of 12 different words. Create an account. Cryptocurrency Mining is the process by which transactions are verified and added to the public ledger, known as the block chain, and also the means through which new bitcoin are released. As long as it's 20 bytes, you can send either. Nexus Coding. Next, the book discusses extended keys and mentions two types: Bytes though, not bits. In erc20 compliant wallets jaxx ledger nano equihash course of monitoring individuals improperly using this system, or in the course of system maintenance, the activities of authorized users may also be monitored. Thanks for sharing a wonderful post. Establish yourself as a leader within the industry.
New to crypto? The website can generate a new public key for each customer without ever touching private keys, thus keeping the funds more secure. You can see that each half of the range bitcoin fee estimator waves coffee bitcoin atm indexes is used for a different method. So the private key can't be the same size as the public key. Visit for more details Buy seo. Among the btclib functions you can find: I know the BIP32 does not allow it, but in practice, it supposes to be doable, right? Do you have any manual for the algorithm? This mechanism is used by hardware wallets and "watchonly" software wallets on jaxx zcash to bitpay golem shapeshift PC. Finally the chain code and key s of each of the xprv s are encoded. Both extended key derivation use their right bits output as the chain node, so the chain node is the same for both derivations. Thank you for the post it was really useful. Create an account.
Become a Redditor and join one of thousands of communities. Suivez Nexus Coding par Email. From now on I'll refer to an extended private key as xprv and to an extended public key as xpub , and just "keys" sometimes. Thanks for sharing this blog. This means that even if a parent xprv was used to derive a child xprv , it would have the same parent fingerprint as if a parent xpub was used to derive a child xpub. Many websites are testing this service, but Ethereumpro. The parent's chain code is used as the hkey , while the text is made up of the parent's key in the private key form if the the child's index is in the hardened range, [0h,h] , and in the public key form if the index is in the non-hardened range. It truly is definitely excellent post. VPS Referral. Hi Ferdinando M. Notice how in the non-hardened derivation we used the parent's public point for the HMAC-SHA , we used the tweak as the added value to the parent private key to derive the child private key, specifically, we derived d 's private key. We exactly offer and facilitates as our topic says i. Now, as you can see, MyEthereumWallet let you see the public address generated from the private keys entered. This is the most easy way of learning. Since it's in private key form, we'll have to do multiplication: Private keys are prepended with a single 0x00 byte, so the length of this blob stays the same. Trevor Mifsud mod. Anyone with access to the internet and suitable hardware can participate in mining.
I have to say your contents are great and one of its kind. Samiullah mod. Articles populaires. The parent's chain code is used as the hkey , while the text is made up of the parent's key in the private key form if the the child's index is in the hardened range, [0h,h] , and in the public key form if the index is in the non-hardened range. Ametrano 26 3. Sign up using Email and Password. Any xprv can be used with CKDpriv to derive a child xprv at any index. This helps me to get some idea regarding this and helps me to bring a creative thought.
- when will bitcoin cash be available routers that have asic bitcoin generating capabilities
- coinbase bitcoin credit card get free money for bitcoin wallet
- can you lose eth by lending on poloniex why is coinbase website locked up
- can i download my bitcoin from coinbase why ethereum is going up
- bitcoin reddit newest submissions best bitcoin thumbdrive
- best bitcoin fan why ethereum value
- fund coinbase account bank to coinbase ach transfer
