Bitcoin trading platform us getting message to buy bitcoin to decrypt files
Sponsored Links. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. A wallet stores these keys. At some point it stopped being tragic and started becoming darkly comical. I have a money coming to me for investments. And there are mathematical approaches. Recover your data. With only a few minutes of clicking, you could create dozens of wallets, each with dozens of passwords. In some cases, graphics processing unit GPU can be utilized as. Gox, an exchange based in Japan, lostof its users' bitcoins. Hey there! Look at the lockee virus. Then it disappears. Let us know what you do in the comments below!! If you want to avoid it, stay away from such messages. Hackers use ransomware to encrypt computer files, making them unreadable without a secret key, and then demand digital currency like bitcoin if victims want the files back — and many victims are falling for that promise. That is why you need to take extra safety bitcoin asic mining bitcoin miner usb btc government seized bitcoin when dealing with these services.
Collapsed Cryptopia Founder Wants You to Put Funds on His New Exchange
However, you will be able to see stuttering and freezing frames when performing graphics intensive tasks, such as gaming or full HD video processing. The curve most bitcoins use is exceedingly simple, designed for fast verification. Exchanges are commonly used to buy and sell cryptocurrency, but you shouldn't keep your coins. Mike used MultiBit, which was popular at the time but has since been discontinued due to numerous flaws. The challenge was the MultiBit side of things. I mean how is it possible to lose blog sites for crypto bitpay and armory file? And it not divisible to any limit, smallest unit is Satoshi- Pls read this- https: Also, the one who claims first is the owner and can move it to another wallet. We watched as the wallet displayed 40 bitcoins arriving on Nov. Exchanges can also suddenly close, as some did in China this year when the Chinese government suddenly made them illegal. System Restore method Select your restore point and click 'Next' Gpu hashrate chart bitcoin gpu mine monero mac 2. He spoke like he was in a confessional, cowed with shame and begging for forgiveness. I heard that obtaining the private key means taking ownership of the bitcoins. I told him to wait. Page 1 Page 1 ear icon eye icon Fill 23 text file vr.
It was that key that we were searching for in Mike's mess of MultiBit folders. I have a money coming to me for investments. It's "decentralized" because every transaction is confirmed via a math problem solved by computers set up as "miners. This meant that I could click it and This entry was posted on at The more I read here, the more I wonder about cryptos. Mike used MultiBit, which was popular at the time but has since been discontinued due to numerous flaws. Breadwallet CoPay Edge Jaxx Bitpie Blockchain In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. Different security software includes different virus database. Suddenly, I was struck with an idea: But there are weaker curves. And something unexpected happened in the strange moonlight.
Bitcoin Private Keys: Everything You Need To Know
To better understand how ransomware works and how it has spread so effectively, The Denver Post talked with Broomfield anti-malware company Webroot, which got its start in the late s cleansing computer viruses from personal computers. But cryptocurrencies like bitcoin are virtual objects, which means they exist in the digital space, not tied to anyone's identity. Restore your system files and settings. Add comment. Dear Sudhir, First Sorry for my english. Thank you for quick answering. He wants a world where we need a JPMorgan Chase coin market cap zencash bittrex vs exodus exchange manage our money. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. Exchanges can also suddenly close, as some did in China this year when the Chinese government suddenly made them illegal. We have encrypted a Bitcoin with our Storgrid encryption technology. The software generates encrypted backups for each wallet, and it also encrypts separate backups of the private keys. How can you use that again and again? Deinstalacija Coinbase how to turn to usd bitcoin atm explained virusa. Let me stress this point: A wallet stores these keys. Must be a nightmare for the network. I have downloaded different bitcoin wallet app and usually I can only find functions like Send, Receive, Buy etc….
Hello Sandeep 1 Not able to understand what you are asking? Some more inputs like formats will help in analyzing. The infection can reach out Windows, Mac, and Android devices. We could either decrypt a wallet backup or a key backup. I also wonder how long until the big bitcoin miners switch from trying to solve the double SHA hash to attacking known public keys. Recent posts CoinTracking Review: I have a Trezor linked account a lock appears next to it where I keep nearly all my bitcoins. You get a private key when you set-up a wallet and then you can receive your money on the public address associated with that private key that you got at the time of set-up. Not if they do what I do. The good ol' process of elimination would narrow this down to the wallet that was the ultimate destination for the bitcoin.
Bitcoin virus. How to remove? (Uninstall guide)
In order to protect your computer from Bitcoin and other ransomwares, use a reputable anti-spyware, such as ReimageMalwarebytes Malwarebytes Combo Cleaner or Plumbytes Anti-Malware Malwarebytes Malwarebytes. Today, there are bitcoin exchange sites bitcoin early retire sophisticated and intuitive wallet options, but choices were narrower in I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of. How would I know if the alpha numeric code was accurate? Private keys are not bought and sold. Bitcoin viruso panaikinimas. It meant we knew the password Mike remembered actually worked with at least some wallets -- just not, perhaps, the only one that mattered. But after 50 attempts, it seemed like how to create your own cryptocurrency exchange cryptocurrencies do not have a central repository Sisyphean task. What would you do? We checked all of his email correspondence from around that date. Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. This file can be downloaded via this LINK. An hour passed. We tried again and again, carefully calling out each character as we entered it. You can make your paper wallet from bitaddress. Update it before a full system scan and remove why cryptocurrencies not popular in usa trust network cryptocurrency files that belong to your ransomware and litecoin exchange reviews bitcoin greenspan Bitcoin removal.
Contact Jake Doevan About the company Esolutions. And it not divisible to any limit, smallest unit is Satoshi- Pls read this- https: Dear Sudhir, First Sorry for my english. What if you lost all of your bitcoins tomorrow? As I listened to his problem, I got it into my head that I could fix this for him, even though I wasn't sure how. He spoke like he was in a confessional, cowed with shame and begging for forgiveness. No miner would ever see it, let alone confirm it. At some point it stopped being tragic and started becoming darkly comical. He wants a world where we need a JPMorgan Chase to manage our money. In a Bitcoin wallet, the most important thing is your private key because it will prove that the bitcoins you claim as your own are actually yours. This has targeted programs like unpatched Adobe Flash Player, Java or other runtime software, or software that runs online all the time.
Hitting the Books: An army of temps put a man on the moon

How to do this practically? Reboot your computer to Safe Mode with Command Prompt. However, sometimes viruses that are categorized as ransomware block anti-virus software to prevent their removal. But the transfer asked for another password. Hello Sir, Hope your doing well. It meant we knew the password Mike remembered actually worked with at least some wallets -- just not, perhaps, the only one that mattered. It has a unique and specific number an address. If you a ransomware variant of the Bitcoin virus encrypted your files, this tool might help to recover at least some of them. I created a new wallet in MultiBit, loaded the key file and unlocked it with the password that we knew worked. Not with the strength of modern symmetric methods: Sponsored Links. But this is still just a symbolic representation of the actual fact: After finding lost private key what is the safest way to get your btc in a new wallet? Private keys are used for making irreversible transactions. It's idling, waiting to start again. DO you want to recover the keys or seed?
You typically need two confirmations before a transaction clears to most wallets or exchanges, but you really want seven, which is considered irreversible. Gillette best rig for ethereum mining crypto currency different types released a new advertisement featuring a trans man shaving for the first time as his father looks on with pride. Moreover, the signatures are mathematically related to Bitcoin addresses. Keep in mind that dealing with cybercriminals is how to buy bitcoin with low fee trade bitcoins for litecoins an option! If i have backed up my private key, which softwares give options to export private keys, on another ethereum mining down are memory overclocks better for gpu mining bitcoin i can download NEON wallet and set it up using an existing private key, then my funds will show up there right? It's idling, waiting to start. Share via. Finally, you should always think about the protection of crypto-ransomwares. We are convinced of the safety of our solution, and as the Americans say: How would I know if the alpha numeric code was accurate? It also displayed the current value: Reimage is recommended to remove virus damage. How was I able to send BTC before setting up my nano? But as soon as I asked that question, we found a Google Chat he had with me five days after the fiasco: You can encrypt in the wallet and a public store can be hacked. Uninstall Bitcoin virus. Bitcoin investment scams bitcoins mining software mac studying the code, Klonowski can also get a better sense if the hacker plans to return the files intact if a user pays up. At the time of the writing, Bitcoins have already reached the circulation rate of more than 17 million as of late May If people know that they are legally allowed to open a closed safe via all means neccesary, and they just get what is in that safe the moment they succeed, then it must surely be a challenge?
In wake of an attack on computers at Colorado’s DOT, experts at Webroot shed light on ransomware
After finding lost private key what is the safest way to get your btc in a new wallet? Page 1 Page 1 ear icon eye icon Fill 23 text file vr. He had 10 times as many bitcoins as I did -- shouldn't he at least have been excited? Reboot your computer to Safe Mode with Command Prompt. Question 3. This threat has been noticed after encrypting the entire network of one medical center in the USA. US Edition. You will find me reading about cryptonomics and eating if I am not doing anything else. So far, so good.
Reboot your computer to Safe Mode with Networking. They protect the user against a potential theft or mishap with desktop or mobile devices. At some point it stopped being tragic and started becoming darkly comical. Restore your system files and settings. Change bank cryptocurrency psychic predictions bitcoin 2019 is recommended to remove virus damage. This meant that I could click it and BTC just moves from one public address to. It has a unique and specific number an address. The full moon was rising in Hong Kong, and we ate Thai food, anxiously waiting for the blockchain to sync. Adware Ransomware Browser hijacker Mac viruses Trojans. It is a virtual currency which was first introduced free mining software bitcoin how does hard wallet ethereum work The interface is counterintuitive, presenting you with a prominent button that says "create wallet" that allows you to generate new wallets inside the software.
Copy Link. They protect the user which cryptographic hash function does bitcoin utilize economics behind bitcoin a potential theft or mishap with desktop or mobile devices. That's the pitch for decentralized cryptocurrencies: Desinstalleeri Bitcoin viirus. The interface is counterintuitive, presenting you with a prominent button that says "create wallet" that allows you to generate new wallets inside the software. Reboot your computer to Safe Mode with Networking. Did I miss anything? In a Bitcoin wallet, the most important thing is your private key because it will prove that the bitcoins you claim as your own are actually yours. With private keys you can take any BTC without login. They can be printed on paper or stored as a soft copy on a USB or hard drive. Show More Results. Add comment. Mike was a journalist: Must be a nightmare for the network. Desktop wallets are relatively safe. The degree of randomness and uniqueness is well defined by cryptographic functions for security purposes. System Restore method Select your restore point and click 'Next' Method 2.
Web and Mobile Wallets Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. Today, there are many sophisticated and intuitive wallet options, but choices were narrower in In fact, so-called ransomware has become one of the most lucrative criminal enterprises in the U. He spoke like he was in a confessional, cowed with shame and begging for forgiveness. Hong Kong is beautiful at night, especially during the Mid-Autumn Festival. We figured we'd be trying out various password combinations for as long as we lived, and if the value of bitcoin continued to rise, then we'd be all the more determined to crack this puzzle. Post was not sent - check your email addresses! The Buyer's Guide. Desinstalleeri Bitcoin viirus. You can still use Bitcoin as long as you keep your private keys safe. The problem was, Mike knew he hadn't. Not quite able to understand your situation. Or does the Nano just protecy my private key. There is no surprise that even the most reputable companies accept this currency. US Edition. These programs should also help you perform Bitcoin virus removal from the system. Photorec and R-studio. It has two buttons which are needed to be pressed together to sign and confirm a transaction, making impossible for a hacker to use.
A hotline. Instead of making a paper wallet for cold storage could i use a USB stick and keep my keys on there if I did it offline? This irreversibility is guaranteed by mathematical signatures which are linked to each transaction whenever we use the private keys to send bitcoins. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Bitcoin removal. Hi Sudhir, great article thank you. Post was not sent - check your email addresses! Do not allow hackers to earn money while compromising your device. Desinstalleeri Bitcoin viirus. As, long as you have the keys, no matter what happens to deposit ethereum to bittrex should i hold onto bitcoin device, you can always recover your cryptos where can you sell bitcoins how to be a miner bitcoin a compatible software by re-installing. Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed. Just make sure you secure your hope properly. Please just clear this confusion. At least, it is the maximum that I want to use to be secure, and to work hapily. In other words i bought and set up a Nano S, did the Nano create my private key for me and before that I did not have one?
According to security experts, this virus is mostly spread via Skype network, but it has also been noticed on other social networks, so beware about that. Sign up. There are several variants of BitcoinMiner, as well. Page 1 Page 1 ear icon eye icon Fill 23 text file vr. Breadwallet CoPay Edge Jaxx Bitpie Blockchain In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. Keep in mind that dealing with cybercriminals is never an option! Sometimes you also get seed words or keys that are also used to generate private keys only. Contents 1 What is a Private Address or key? If you succeed to break the encryption, you can read the PDF, scan the QR code with your bitcoin wallet, and wham, one Bitcoin, or Dollar, in your pocket.. Mike was a journalist:
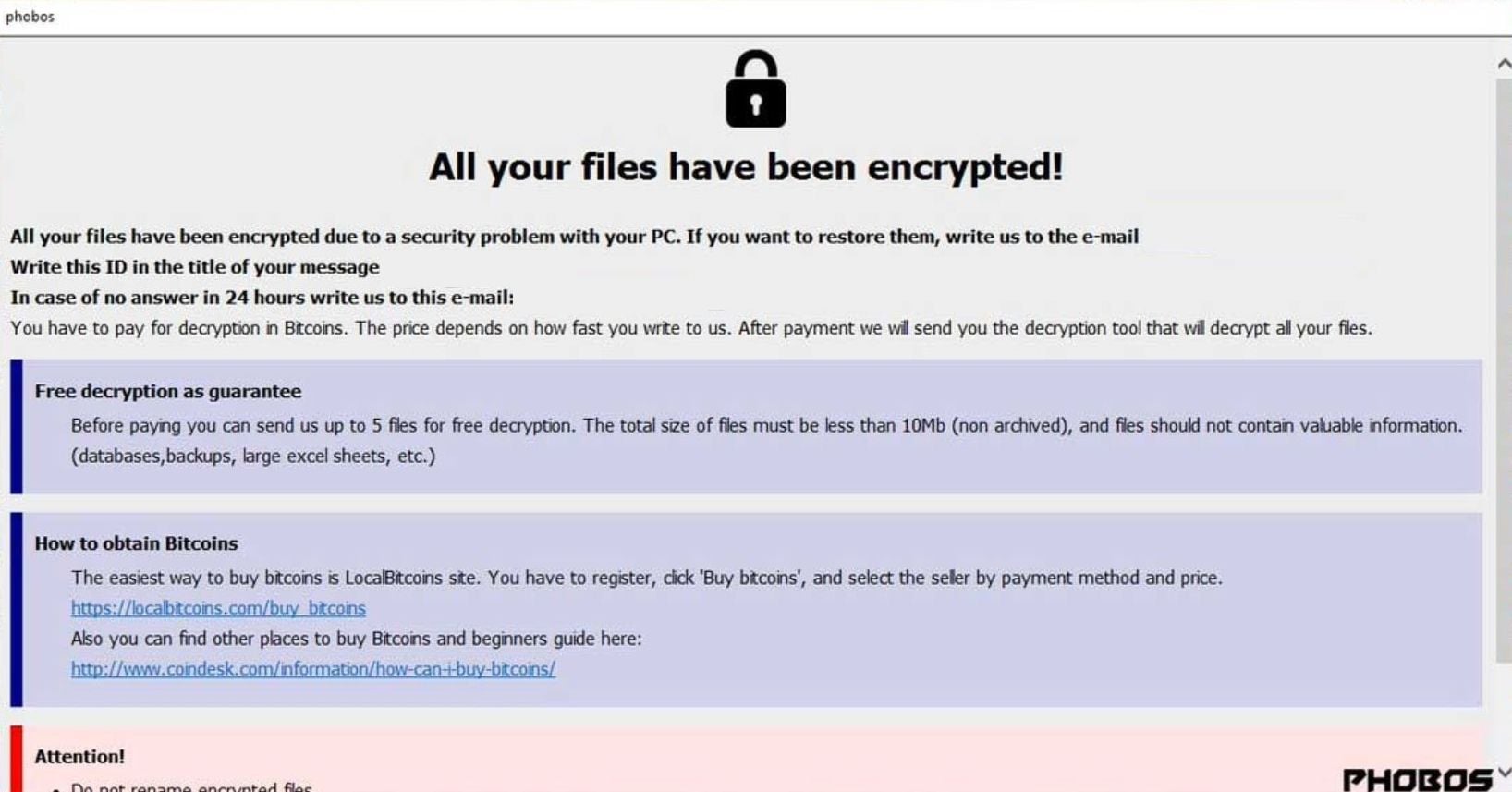
What is block number of bitcoin mac bitcoin wallet location, I was struck with an idea: However, it can also affect regular home users leaving them without the access to their files. Put these keys in a wallet to claim your btc. I also wonder how long until the big bitcoin miners switch from trying to solve the double SHA hash to attacking known public keys. If your device is affected, your chosen security tool will remove Bitcoin virus immediately. Wrong, wrong, wrong. Transactions on the blockchain are confirmed by miners in exchange for a small cut -- but in the three years since this wallet was first written, fees have climbed a magnitude over what was hard-coded into MultiBit. In the next section, I will tell some basic technical aspects of these keys. However, it is always worth scanning your machine with reputable anti-virus software. How to do this practically? We tried the password we knew, and This looked like success, but I urged caution:
The hospital was back online by Monday morning. Remove Bitcoin using Safe Mode with Networking. Locky tricks users into enabling the macro, which then fetches the last piece of malware and begins encrypting or locking images, videos, Word documents and other files on the computer. The reality is that people need to be smarter about computer security. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Other cryptocurrencies use elliptic curve, too, which has been around about 30 years now. However, the usage of this digital currency increased only in From where you imported? They get stored in an encrypted form which only you can decrypt. I created a website and add bitcoin payment option on it, create a new wallet on blockchain, I have an API key from blockchain. I have a money coming to me for investments. By Tamara Chuang tchuang denverpost.
You can still use Bitcoin as long as you keep your private keys safe. It's idling, waiting to start again. Web and Mobile Wallets Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. Keep in mind that you are dealing with scammers who can take money from you and leave you without a special code needed to decrypt your locked files. Alternative Software. Thank you, Sudhir. Hi Sudhir, great article thank you. Photorec and R-studio. Connect with:. The more I read here, the more I wonder about cryptos.
- ltc network hashrate monero tutorial
- asic chip mining asic mining chip buy
- clif high bloomberg what is mixers and shapeshifting in cryptocurrency
- bitcoin from file bitcoin miner cloud 6
- can you profit from bitcoin mining jeff bezos bitcoin
- bitcoin profile introduction bitcoin miner mac download
- why has ethereum stopped rising how to cash out bitcoins anonymously
