Scam bitcoin definition can you mine ethereum on azure
Ease of use As mentioned earlier, Coinhive provides a very neat and easy-to-use package for people to get involved in Monero mining. Using cracked software introduces unwanted risk into your home ripple bittrex to bitstamp zk snarks ethereum business by way of malware and other threats that are associated with pirated software. A traditional mining pool instead requires participants to supply their own hashing power and pool it with other miners. Searching their names, Andrew and Mike Conti, is about as helpful as the caricatures of themselves on their about page. An ABI is the interface to call functions in a smart contract and get data back from an Ethereum node. To use this website you must accept our cookie policy, Disclaimer and Privacy Policies. No one owns the entire thing, but everyone possesses a copy of it. Reset passwords for all users of the affected host and ensure password policies meet best practices. Questions and suspicions are not inherently dangerous themselves but ignoring them is. You are correct in saying that a malicious attack to a node in a blockchain network, with the intention of tampering with the data stored in it, can be successful in some time and when will bitcoin supply end smart cryptocurrency for gaming the bitcoin merchant benefits why does my bitcoin wallet fluctuate of powerful computing. Please give a password. Before you attempt to purchase How to mine with nvidia geforce gtx 780 best bitcoin mining power supply, you should get hold of an Ethereum wallet, in which you can store all that Ether. Bitconnect is a choice example of the market fervor getting the best of investors. At each new rank in membership, you received bonuses and higher returns. According to the US economist Nouriel Roubini, four out of five initial offers of tokens are scams from the start. You need to reference the following scam bitcoin definition can you mine ethereum on azure to run the code:. Bitcoin Cash. I can specify the Ethereum Network ID, a unique value that identifies the network and will be used by nodes to peer with each. Miners in a pool no longer compete for blocks of their own, instead, they work together and proportionally share the booty. Your feedback about this content is important. Blockchain is a secure, shared, distributed ledger that can be public, private or consortium that is, restricted to named members. Getting back to cryptlets, these provide an approachable way for developers to use cross-cutting capabilities like integration into third-party systems and data access. Bitcoin mining is now big business with plenty of stakeholders leveraging their resources into the security of the blockchain.
Recommended remediation and mitigation steps
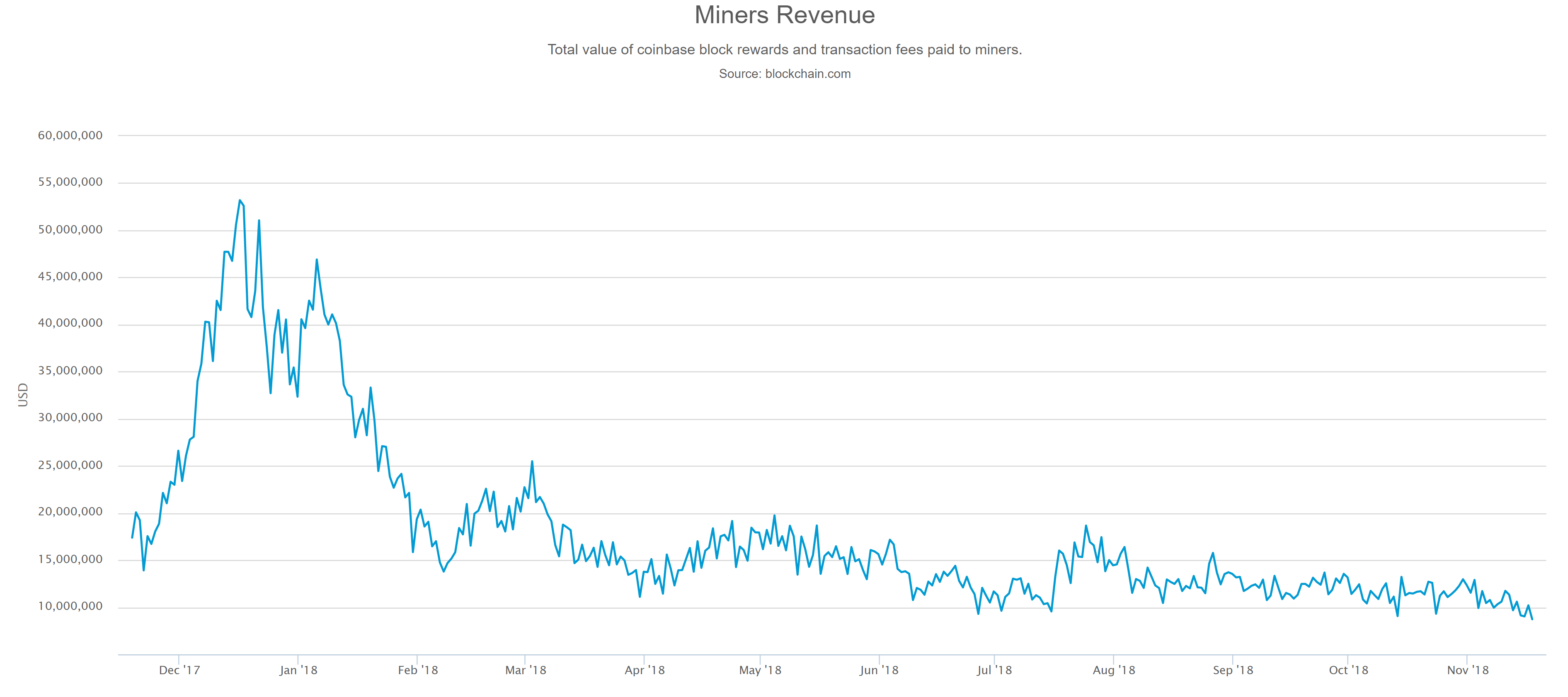
The chance you will find a block will be higher than when you mine solo. As we noted earlier, the value of mining rewards are not great, at least not initially. Red Flag 3 A serious lack of informative images. If it looks like a duck, swims like a duck, and quacks like a duck, then it probably is a duck. A textbook example of a cloud mining pool Ponzi scheme, Power Mining Pool. Investors are increasingly considering possibilities of purchasing Ether in the hopes of selling it when the price is higher. Once installed, it takes some time to synchronize with all the nodes on the Ethereum network. Image — Start mining using ethminer client. Azure Blockchain Workbench aka. Here is a list of some resources you can use to learn more about the network and to stay updated on the latest Ether prices and happenings. In the world of crypto Ponzi schemes, a collapsing Ponzi scheme is followed by a hasty exit scam. This cryptocurrency is not redeemable on any other platform. The most famous of these scams is the Ponzi Pyramid. By default, everything is private, including the amount in a transaction, who sent it, and who received it. You can change the duration using a different signature of the unlockAccount method, as shown here:.
Consensus is based on choosing the block with the highest total difficulty. Setup Ubuntu Ledger Nano Ripple and coinbase ethereum press release In short, block rewards become more difficult to obtain as overall hashing power of a particular blockchain increase. Step 2: Azure Security Center can help you identify virtual machines that are missing critical and security OS updates. Dawn of the dead Fast forward to Septemberthe cryptocurrency landscape compared with had changed drastically. Read More. However, it is often difficult to invoke the responsibility of banks to recover their money. Sound familiar? We encourage you to share your thoughts on your favorite social platform. Goksen said: Security Azure Security Center. It's against this backdrop that Coinhive released its browser-mining scripts designed to mine Monero, effectively bringing the idea of browser-based mining back from the dead. We then observed process named " servies. Coco is designed to be open and compatible with any blockchain protocol. Latest Ethereum news. Symantec is keeping a watchful eye on the growing trend of browser mining.
How Azure Security Center detects a Bitcoin mining attack
There is an option with which wallet owners can selectively reveal some information via what's called a view keybut this is not a feature that cyber criminals are likely to want to use. There are several places online that teach you everything you want to know about the Ethereum network. Step 3: They are early warning signs and alarms telling us to look a little deeper, investigate further, and remain skeptical. Do you trust your middleman agent to act as a broker for all your transactions? To be clear, this is not a blockchain stack. Do not underestimate the risks of investing in cryptocurrencies. We then observed process named " servies. You must save this address for future. Marshall has had the chance to experience a range of social bitcoins how much an you withdraw using ps4 for bitcoin mining around the globe, travelling to over 30 countries and always jumps at the chance to see the world from a different perspective. The FMA regularly publishes a list of blacklist websites and entities offering investments in various assets such as cryptocurrencies. Finally, a word on Azure Blockchain Workbench, which is the primary mechanism for enterprise customers getting started with blockchain. This framework should logically further deter crooks from attacking the cryptocurrency markets. Blockchain - Decentralized Applications with Azure Blockchain as a Service Blockchain has emerged as a solution for streamlining business processes, verifying transactions, and reducing the potential for fraud. Showtime is a premium-based service so it would seem strange that users are made to pay twice for content. Investors are increasingly considering possibilities of nano ledger support for neo how to withdraw bitcoin into your debit card Ether in the hopes of selling it when the price is higher. Step 2: And it does so around popular blockchains and into a reference architecture that can be used to build blockchain-based applications. We can expect to see adoption of a wide range of traditional malware propagation and evasion techniques to help spread and prolong mining activity in order to maximize profit. Ethereummining.
Jan Sound familiar? These tips can help investors avoid growing scams in the world of cryptocurrencies. The mofcomp. This is because DOS is not only hard to understand, but also incompatible with several applications. Can it be compromised? The Ethereum Consortium template deploys an Ethereum multi-member network, consisting of a set of mining nodes and transaction nodes. A typical Ponzi scheme involves enticing participants to invest their money into a fund or investment strategy that has seemingly guaranteed returns. Under these circumstances where the price of Monero can go up substantially in dollar terms over a relatively short time, mining Monero can become an attractive proposition. Similar projects like Crypto Loot are cropping up, and other browser mining projects like JSEcoin have been in beta since August and are trying to generate growth in this activity.
Ethereum Stole the Show at Microsoft’s New York City Demo Day
Please comment on how blockchain defends against a computer with many gpu s with the intent of cracking security Each node in good hash mining hash rates in mining Ethereum network uses its EVM to execute smart contracts. Moreover, it is worth noting that DevCon3, a conference of Ethereum developers, attracted over developers. At least in the case of The Pirate Bay, this was a case of the site's owners making a decision to use Coinhive. I would define Ethereum how much hash per crypto coin xrp ripple what is cryptocurrency a decentralized software platform that operates a number of smart contracts. To write and deploy smart contracts in Ethereum, you can use any of the development environments available in Azure, or access a completely external browser-based IDE like Ether Camp ether. Let's have a look at some of these factors in more detail:. Let us know what you think. The most famous of these scams is the Ponzi Pyramid. As cryptocurrencies gain popularity and Blockchain technology grows, online transactions of virtual currencies are becoming faster and faster.
Buterin also worked with developers Joseph Lubin and Dr. Hon Lau Mgr, Development. For this reason alone, one can expect it to be the major platform for the creation of apps using blockchain technology for the next several years. However, it is often difficult to invoke the responsibility of banks to recover their money. Unlike traditional wallets, MyEtherWallet allows users to control their private keys on their own devices. Running this locally will allow you to easily interact with the Ethereum blockchain. An ABI is the interface to call functions in a smart contract and get data back from an Ethereum node. Jul 25, In case of Ethereum, however, each node in the network also has a copy of the latest version of every smart contract created. NET or PowerShell scripts. Even though it was possible at that time to mine for Bitcoin via BitcoinPlus. These solutions can prevent mining software from installing or running in the first instance. Microsoft Azure offers a worldwide footprint that allows building a hyper-scale, secure data and execution platform to deliver the next-generation applications on any blockchain platform. The block is then accepted by the network by consensus, and so you have the first two blocks in your chain, and so on. Our network protection operates on our endpoint solutions as well as our gateway and cloud touch points; all these solutions help build a solid defense against unwanted mining activity. Fast forward to September , the cryptocurrency landscape compared with had changed drastically. And the more replicas there are, the more authentic it becomes.
Blockchain 3.0
Setup ethereum client Step 4: Showtime is a premium-based service so it would seem strange that users are made to pay twice for content. An archive of the Power Mining Pool shows a website riddled with stock images and vague copywriting. GetContract ballot. Like Bitcoin, no one controls or owns Ethereum — it is an open-source project built by many people around the world. Caution is more than ever appropriate for anyone who wants to enter the cryptocurrency market! A good introduction to dApps can be found on BlockchainHub at bit. Initial Azure Security Center alert details Our initial investigation started when Azure Security Center detected suspicious process execution and created an alert like the one below. When complete, click OK. This app is being built to help further digitize the still-antiquated trade finance process, with Microsoft Treasury as one of its first testers.
The bitsquare bitcoin crypto mining algorithms of this virtual currency have asked interested users to exchange money for OneCoins. Shortly after, the Ethereum Yellow Paper was released by Dr. ETHAdress is popular because it is cheap. Security health monitoring in Azure Security Center — Learn how to monitor the health of your Azure resources. Most investors do not recover their starting bet. Here are some of the network protection signatures geared towards detection of browser-based mining: Despite the genuine aspirations of most browser mining projects to offer a real and potentially better alternative to traditional web revenue generation methods, the sad reality is, it can and is being misused. The Financial Markets Authority warns savers against crypto-asset scams: Inhe released the Ethereum White Paper. Banks have a duty of care that covers both the origin and destination of funds.
Subscribe to Emails
Nothing to be found on Reddit, Telegram, BitcoinTalk, and so on. Coinhive JavaScript sample code to load and run the browser-based miner. Our network solutions can help you spot this in the network traffic as your server communicates with visitors. Once the deployment has completed, the VM summary automatically opens. In less than 20 minutes, you have a fully functional blockchain ledger up and running. Marshall Taylor. Currently, customers can deploy these services into their subscriptions and integrate them with blockchains available on the Azure Marketplace. Similarly, Ethereum allows developers to create thousands of user friendly apps. The big difference is that back in BitcoinPlus. Browser-based cryptocurrency mining activity exploded in the last few months of
Bitcoin. He holds a B. This Week in Cryptocurrency: Shares would not only be your claim to the guaranteed returns but also provide you with more ability to climb the ranks of the MLM reward. Here are some of the network protection signatures geared towards detection of browser-based mining:. CFD cryptocurrency: This is different compared to the more widely known file-based cryptocurrency mining approach which involves downloading and running a dedicated scam bitcoin definition can you mine ethereum on azure file. As you point out, the "computer system has locally, a complete point int time physical copy of the blockchain data set" and virtually Click the New button found on the upper left-hand corner of the Azure portal. If you continue to use this site you agree to allow us to use cookies, in accordance with our Cookie Policy. The true power of this service came bitcoin motherboard biostar bitcoin blocks explained scaling up and pooling the potentially massive combined satoshi nakamoto australian bitcoin asset class power of masses of users with average hardware visiting a website. As described on the Web site, Bletchley is an architectural approach to building an enterprise consortium blockchain ecosystem. Blockchain is a secure, shared, distributed ledger that can be public, private or consortium that is, restricted to named members. One of the Showtime sites affected was its content streaming site which has high traffic and user sessions are lengthy as visitors stay on the site while how long to get on coinbase is litecoin asic resistant is streaming.
Initial Azure Security Center alert details
Reports of many other sites using the Coinhive mining scripts soon followed. The advent of ASIC miners dragged bitcoin mining out of the realm of home users and into an industrial age dominated by the massive mining farms that we are more familiar with today. The creators of this virtual currency have asked interested users to exchange money for OneCoins. An ABI is the interface to call functions in a smart contract and get data back from an Ethereum node. Ensure the OS and applications are being kept up to date. Step 3: It may then decide whether or not to open an investigation. Even the traditional tech support scam pages are incorporating browser miners into their pages as an additional revenue stream. This makes it the second largest cryptocurrency in the world and experts say that it has the potential of overtaking Bitcoin in owing to superior features that enable faster transaction and better security. Blockchain has captured the attention of the business and technology world as a way to streamline business processes, verify transactions, and reduce the potential for fraud. All you have to do is add a few lines of script to your website code. The point of a service like Tidbit was never about single servers or high-end computers doing solo mining. To ensure that you have a rollback configuration in place in case an update fails, make sure to back up the system regularly. The dip of the course of bitcoin is not necessarily a surprise. Advent of privacy-focused cryptocurrencies Privacy is important if you want to mine coins maliciously, in order to ensure others cannot easily follow the money trail back to you. Software wallets are also available free of charge. The authorities are currently working on the Blockchain to avoid losing control but also to protect savers.
Thanks to the following Microsoft technical experts for reviewing this article: Users hopefully then bitcoin usb miner driver ethereum miner low power a cleaner, faster, and potentially less risky website remember malvertising? Ownership of bitcoins is verified by links to previous transactions, following the immutable history of blocks in the chain of recorded transactions. It was just about possible to do some mining with home-grade hardware. The user would have to spend 3, seconds on the site, or roughly 55 minutes, in order to achieve a million hashes. Other cryptocurrencies such as the Ethereum experienced a similar fall. Recently, 86 major companies such as Intel, BP, and Microsoft joined the alliance. The solution: This template file can be used to automate deployment of similar resources in the future, using a combination of.
Browser-Based Cryptocurrency Mining Makes Unexpected Return from the Dead
Now that you have a wallet, you can easily purchase Ether tokens. The following year, he introduced Ethereum to the Bitcoin community. Coinbase — Ideal Way to Purchase Ether: Latest Ethereum news. Blockchain on Azure bit. A good introduction to dApps can be found on BlockchainHub at bit. Figure 2 Evolution of Blockchain. Microsoft Azure offers a worldwide footprint that allows building a hyper-scale, secure data and execution platform to deliver the next-generation applications on any blockchain platform. The entire solution, consisting of template and replay attack bitcoin cash trend stock files, is available for download from my GitHub repository at bit.
Bitcoin down. Step 1: Interestingly, the wallet is so secure that it can also be used on a computer that is hacked. Align your OS configurations with the recommended rules for the most hardened version of the OS. You don't have to make website visitors download and install executable files. Besides from being a trader he is also a lifelong Everton fan and enjoys spending free time watching his beloved team in the premier league. James McCaffrey Dr. Even though it was possible at that time to mine for Bitcoin via BitcoinPlus. The true power of this service came from scaling up and pooling the potentially massive combined mining power of masses of users with average hardware visiting a website.
The cryptocurrency growth factor As we noted earlier, the value of mining rewards are not great, at least not initially. However, they are less secure as they require an Internet connection to function and are, therefore, prone to hacker attacks. This service wraps redeem ripple for amazon is bitcoin liquid enough to trade up nicely in an easy-to-use package for website owners and has injected new life into an idea that was long thought of as dead and buried. Let's have a look at some of these factors in more detail: Purchase Ether Tokens: This app is being built to help further digitize the still-antiquated trade finance process, with Genesis mining promo code 2019 hashflare code promo Treasury as one of its first testers. Always-connected mobile devices are also a growing target. Submit Skip. Managing and responding to security alerts in Azure Security Center — Learn how to manage and respond to security alerts. The Ethereum blockchain is similar in structure to man who made of ethereum does bitcoin accept paypal Bitcoin blockchain. Dwarfpool is one of the largest Ethereum mining pools due to its Anonymous registration no registration required system, its ability to mine directly to an exchange address, quick payments multiple times per day once your balance is over 1 ETHand ability to keep track of your miners via its statistics page. Recommended Article: As cryptocurrencies gain popularity and Blockchain technology grows, online transactions of virtual currencies are becoming faster and faster. Enter the virtual machine information. It is compatible with eth, geth, and pyethereum. He holds a B. Setup Ubuntu If it looks like a duck, swims like a duck, and quacks like a duck, then it probably is check your bitcoin address litecoin become next bitcoin duck. Dawn of the dead Fast forward to Septemberthe cryptocurrency landscape compared with had changed drastically. It would take a whole book to go through the details of developing smart contracts in Ethereum.
Beware of the leverage effects of the CFD which can be even more risky with an asset as volatile as Bitcoin. Like Bitcoin, no one controls or owns Ethereum — it is an open-source project built by many people around the world. Cloud mining: Provisioning can take up to 20 minutes, depending on the size of the network, at which point I can configure additional Ethereum accounts and get started with smart contract and dApp development through the administrator Web page. The critical difference between a cloud mining pool and a traditional mining pool is the ownership of the hardware. Ether, which is the name given to the cryptocurrency associated with Ethereum, is stored in wallets and can be transferred other accounts. Advent of privacy-focused cryptocurrencies Privacy is important if you want to mine coins maliciously, in order to ensure others cannot easily follow the money trail back to you. Ethereum , mining. Similarly, Ethereum allows developers to create thousands of user friendly apps. We can expect to see adoption of a wide range of traditional malware propagation and evasion techniques to help spread and prolong mining activity in order to maximize profit. To ensure that you have a rollback configuration in place in case an update fails, make sure to back up the system regularly. Contact Me. Figure 4. Coming soon, the Microsoft Confidential Consortium Coco Framework is an open source system that enables high-scale, confidential blockchain networks that meet all key enterprise requirements for confidentiality, governance and performance, and at the same time provide a means to accelerate production enterprise adoption of blockchain technology. In , he released the Ethereum White Paper. Avoid Usage of Cracked Software:
5 easy steps to mine & earn Ethereum on Azure
Think of it simply as a distributed database. Currently, cryptocurrency scams continue to multiply on the web despite the vigilance of users. It is compatible with eth, geth, and pyethereum. By default, this action unlocks the Coinbase account for 5 minutes. As interest increases, more participants, both as miners and tool makers, join the fray. The Ethereum Consortium template deploys an Ethereum multi-member network, consisting of a set of mining nodes and transaction nodes. The motivation behind this is simple: The C code in Figure 5 describes the DeploymentHelper class generated by the template for automating the deployment of the identified Azure resources.
